4 Impacts of MPoC on Mobile Payment App Security

According to recent research, SoftPOS user base will grow 475% globally by 2027 thanks to the increasing adoption of contactless payments. The Payment Card Industry (PCI) has just released their Mobile Payments on COTS (Commercial-off-the-Shelf) devices (MPoC) standard, which will eventually become the standard for certification of SoftPOS solutions.
Because MPoC does not require any specialized hardware (like a card reader) and allows acceptance of payments on any mobile COTS device, there is a shift in focus from hardware device trust to mobile application security. This means organizations with mobile payment options cannot rely on the underlying hardware anymore to secure financial transactions.
In this article we will show 4 potential impacts on the security posture of your mobile payment apps and SDK due to the introduction of the MPoC certification standard.
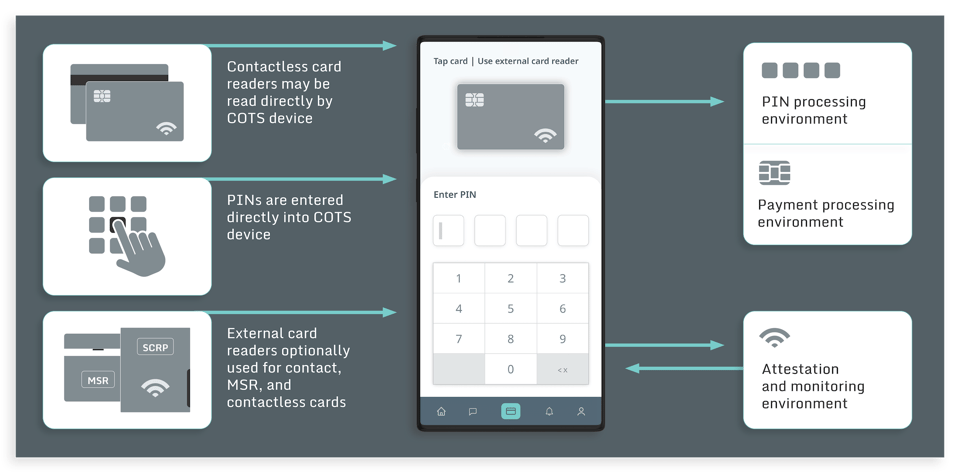
1. Increase in use cases requiring mobile app security
The previous PCI standards relevant for mobile applications were incomplete and they didn’t cover the increasing number of use cases that the wide-spread adoption of mobile apps can support. Specifically PCI used to address only the following cases:
- Contactless payment with COTS accepting PIN entries from customers but requiring the merchants to use additional card reader hardware (PCI SPoC)
- Contactless payment with COTS without requiring the merchant to use additional card reader hardware and without requiring the customer to enter a PIN code. But that use case would be possible only for payments below a defined Card Verification Method (CVM) limit. (PCI CPoc).
This new MPoC standard will eventually replace both above-mentioned standards and become the standard for SoftPOS SDK solutions and merchant-based payment acceptance applications. By facilitating the acceptance of payments on mobile devices by both SMBs and large retailers, the result will be that mobile payment solutions will be accepted around the world at a much broader scale.
2. Objective-based security requirements will allow more app design freedom
PCI standards are maturing and evolving toward objective resilience requirements; however, these are purely for software-based payment applications. Based on PCI’s Attack Costing Framework, the MPoC certification standard is the first to include minimum resilience requirements for protecting encryption keys, patent assets, application code protecting patent assets, and integrity of the Attestation and Monitoring (A&M) component. As the MPoC standard is less prescriptive than prior standards on how to achieve this security, SoftPOS developers will have much more freedom in deciding how to achieve the standard. Strict guidance on the solution’s architecture is no longer included, and the expectation is that similar objective-based resilience standards will be emerging in other software-based certification programs in the future.
3. Payment related functions will move out of the app and into a shared SDK
Prior to the introduction of the PCI MPoC standard, it was common to develop a PCI-compliant app and distribute different flavors of it using a white-label approach. As the new MPoC standard explicitly differentiates between the MPoC SDK (which implements all core payment-related functions, including their own UI components) and the application which provides the overall functionality and integrates payment processing as a component, there will be an increased shift to a library-based distribution model. The SDKs will evolve to support full SoftPOS solutions, supporting both the consumer side payment initiating function and the merchant side payment acceptance function. Like "super SDK's" which support both initiating and accepting payments, for basically any payment use-case, the SDKs may also support their own UI. This leaves app developers to simply integrate them to provide an end-to-end solution analogous to Venmo, Paypal, or Vipps.
4. A fully integrated security architecture will be critical
With the increased focus on Attestation and Monitoring, in order to deliver a secure and excellent UX, the MPoC standard clearly requires tight and secure integration between the client and server-side, to consistently guarantee the integrity of the COTS device and the SoftPOS application. While the server-side component can take care of the complete attestation of both device and application, the client-side payment component within the mobile app needs to interact with the backend at defined time intervals and before initiating any transactions. The client-side component also needs to provide a first layer of defense and, at a minimum, support partial attestation when no connection with the backend is possible, for legitimate offline payment processing. This will require client-side Runtime Application Self Protection (RASP), with checks at startup and throughout the code, which can autonomously halt the application, even when running in offline mode. For example, this may be applied in cases where the attacker is able to disable communications with the Attestation and Monitoring backend.
How Guardsquare can help meet MPoC requirements
With more functionality on the mobile side, protecting the code is a necessity.
With functionality increasingly being moved onto the mobile device, attackers can leverage insights into your app’s architecture and software to modify or defeat the functionality of different mobile app components. This makes it critical for the code of a mobile app to be hardened and protected. Guardsquare offers complete solutions to address this need. DexGuard and iXGuard, provide multi-layered code hardening solutions of the SoftPOS through a number of capabilities. These include multiple code obfuscation techniques, data encryption, and RASP, among others. ThreatCast, Guardsquare’s mobile threat monitoring solution, provides real time insights into relevant runtime threats and can be easily fed to your backend Attestation and Monitoring service. In addition, Guardsquare’s free mobile app security testing tool, AppSweep, can be easily and transparently integrated into the application development process to scan code for potential vulnerabilities.




