-
Products
-
Solutions
-
Resources
-
Company
- Pricing
Products
Solutions
Resources
Company
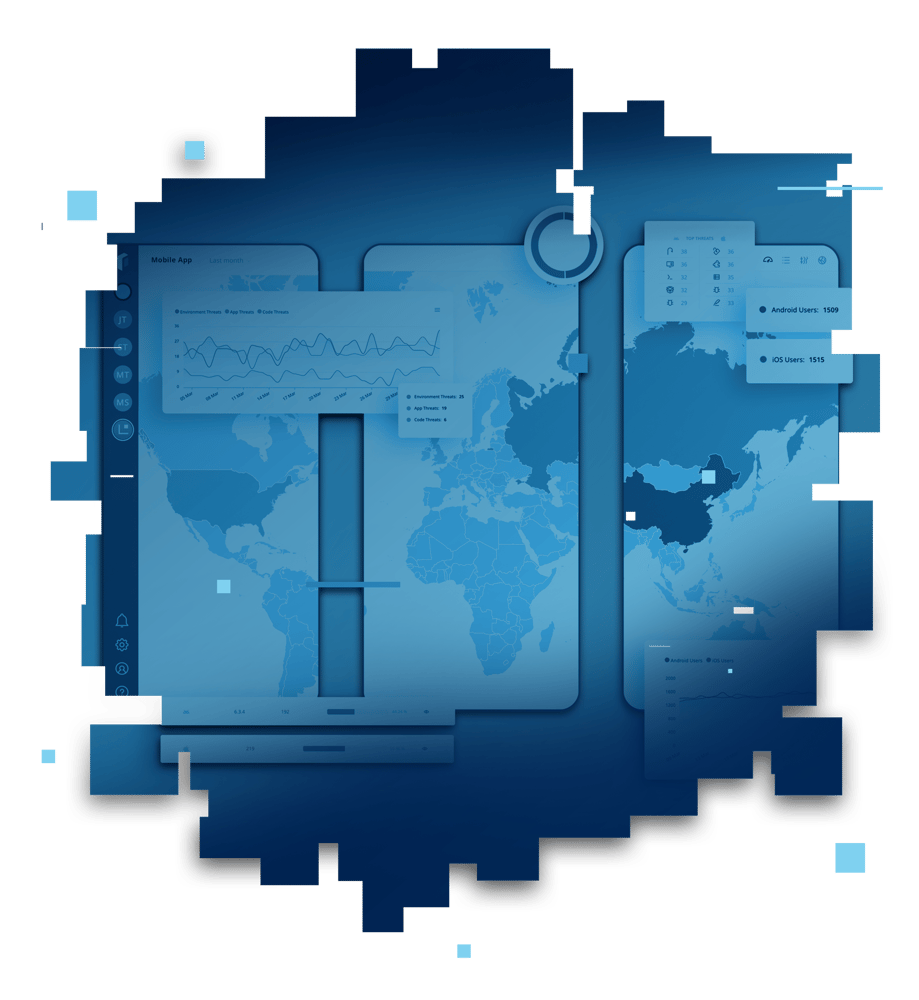
Security doesn’t end after development — use threat monitoring to gain insights into real-world attack vectors and detect suspicious activity and to inform your security configuration.
Secure software development can mitigate risk, but it can’t eliminate it; adopting threat monitoring technology enables developers to gain intelligence into where your app’s greatest security gaps are and identify what steps to take to close them.
Consolidate runtime application threat information with data from your customer relationship management or fraud monitoring systems' data to identify suspicious devices, detect fraud and prevent malicious activity.
Research shows that despite developers' priorities, mobile apps still aren't secure enough.
Too often delayed to the end of the development lifecycle, security needs to be considered right from the start. As your app development progresses, testing, feedback and monitoring help you to ensure the highest possible level of security.








Mobile app security is most effective when it’s considered from the outset of the development lifecycle, which includes making informed design choices, following best practices as well as early rounds of testing and refinement. Ultimately, engaging in secure software development practices identifies security risks early, when they’re quick and cheap to fix, rather than after deployment.
 Mobile app security is most effective when it’s considered from the outset of the development lifecycle, which includes making informed design choices, following best practices as well as early rounds of testing and refinement. Ultimately, engaging in secure software development practices identifies security risks early, when they’re quick and cheap to fix, rather than after deployment.
Mobile app security is most effective when it’s considered from the outset of the development lifecycle, which includes making informed design choices, following best practices as well as early rounds of testing and refinement. Ultimately, engaging in secure software development practices identifies security risks early, when they’re quick and cheap to fix, rather than after deployment.
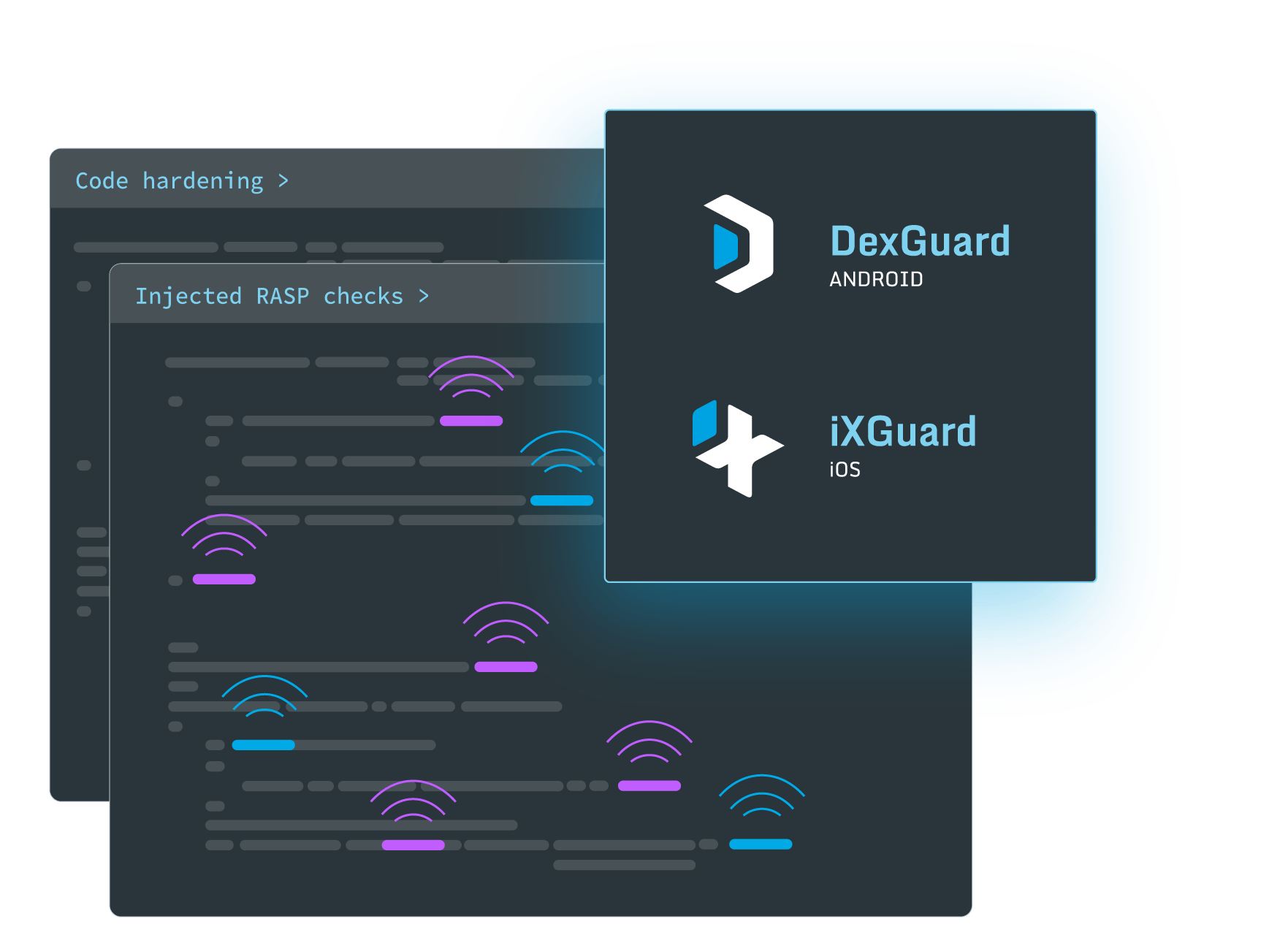
Now that your app is implemented, it’s crucial that you incorporate defenses against reverse engineers in order to protect your intellectual property, prevent counterfeits and secure your data and your brand’s reputation. App shielding techniques like code hardening and runtime application self-protection (RASP) ensure that your mobile app can’t be easily reverse-engineered or tampered with.
 Now that your app is implemented, it’s crucial that you incorporate defenses against reverse engineers in order to protect your intellectual property, prevent counterfeits and secure your data and your brand’s reputation. App shielding techniques like code hardening and runtime application self-protection (RASP) ensure that your mobile app can’t be easily reverse-engineered or tampered with.
Now that your app is implemented, it’s crucial that you incorporate defenses against reverse engineers in order to protect your intellectual property, prevent counterfeits and secure your data and your brand’s reputation. App shielding techniques like code hardening and runtime application self-protection (RASP) ensure that your mobile app can’t be easily reverse-engineered or tampered with.
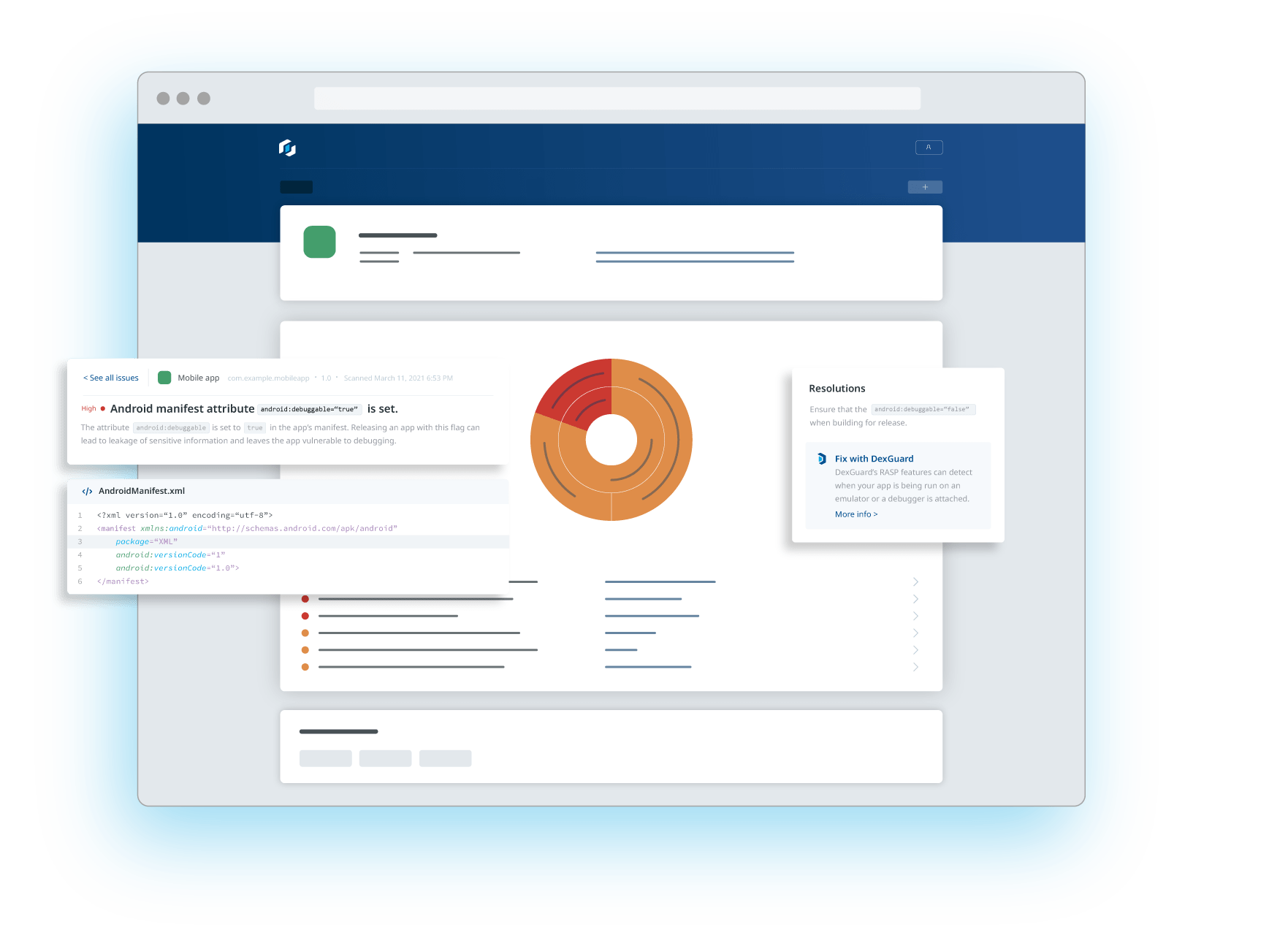
You wouldn’t release your app without testing its functionality; nor should you without testing its security. Pentesting, or penetration testing, is often performed by third-party experts to attempt to identify security gaps in your app and gain insight into its internal logic, just as a threat actor would. A complement to pentesting is AppSweep, Guardsquare's automated mobile application security testing (MAST) tool.
 You wouldn’t release your app without testing its functionality; nor should you without testing its security. Pentesting, or penetration testing, is often performed by third-party experts to attempt to identify security gaps in your app and gain insight into its internal logic, just as a threat actor would. A complement to pentesting is AppSweep, Guardsquare's automated mobile application security testing (MAST) tool.
You wouldn’t release your app without testing its functionality; nor should you without testing its security. Pentesting, or penetration testing, is often performed by third-party experts to attempt to identify security gaps in your app and gain insight into its internal logic, just as a threat actor would. A complement to pentesting is AppSweep, Guardsquare's automated mobile application security testing (MAST) tool.
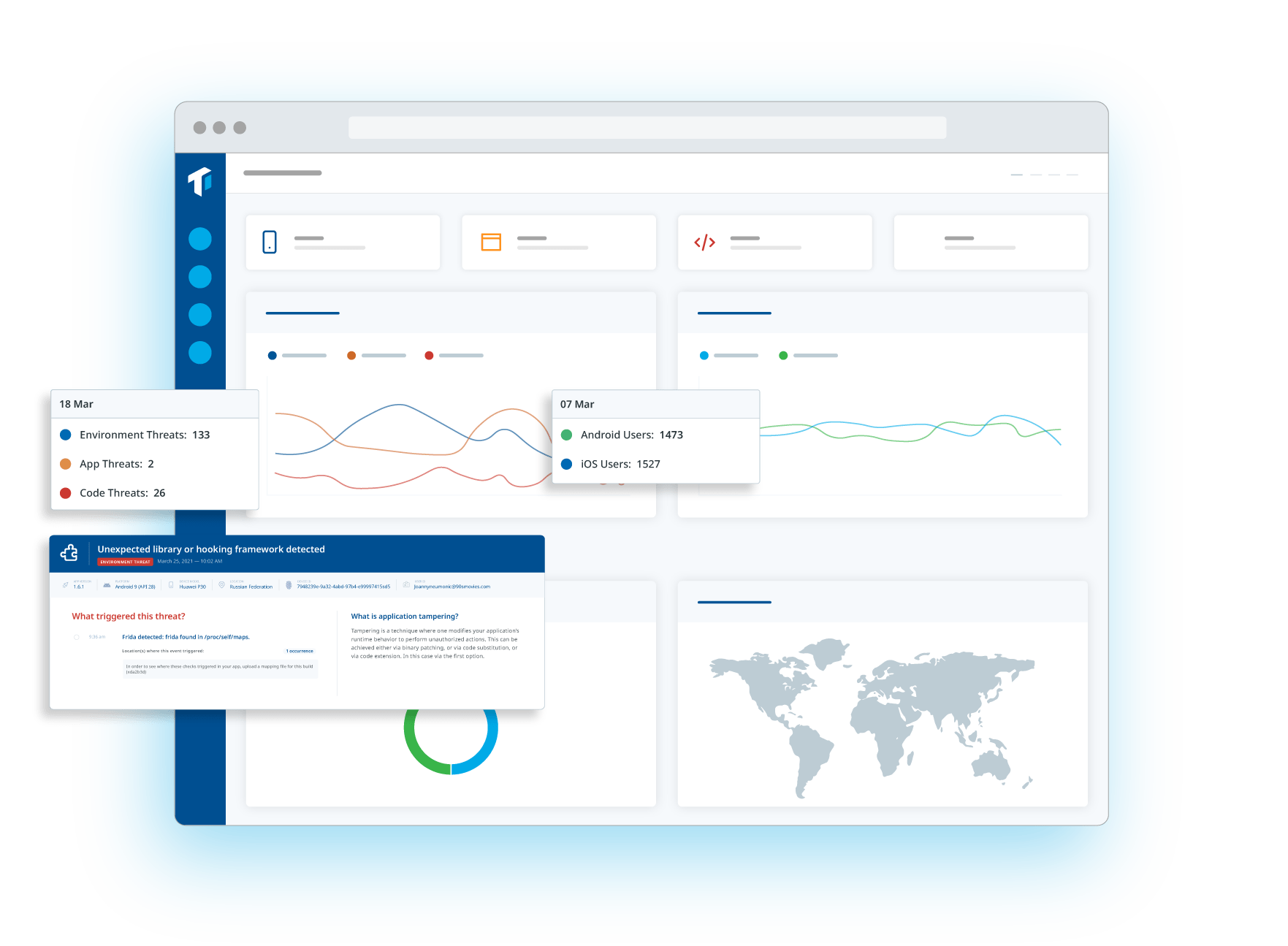
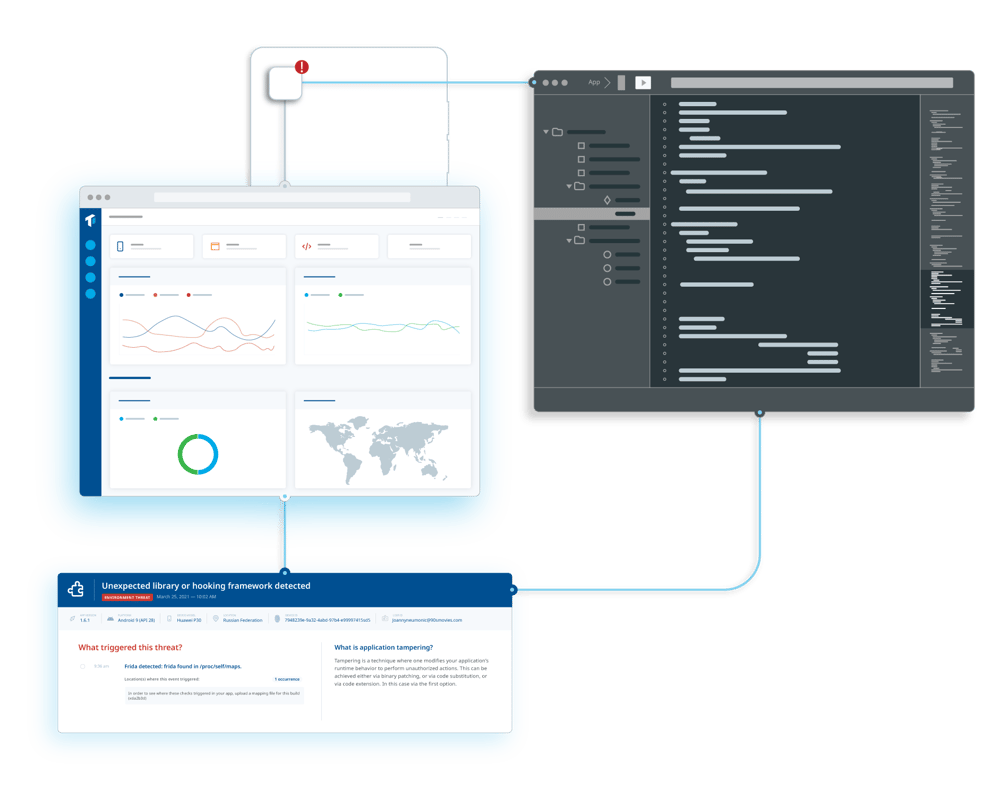
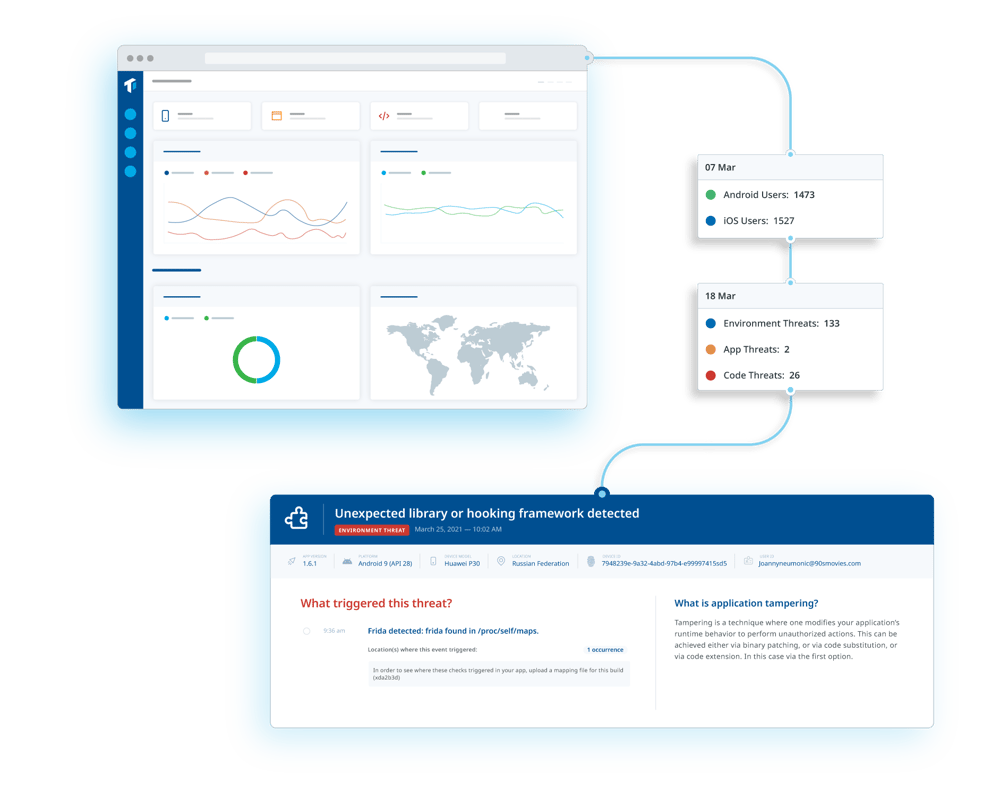
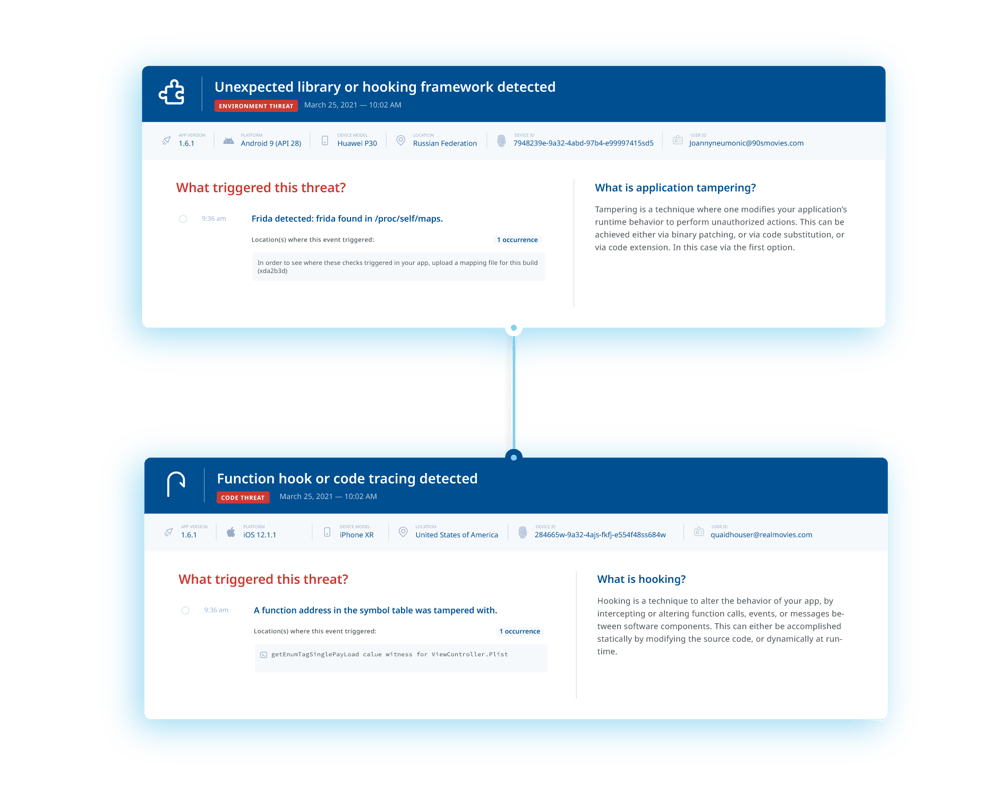
Now it’s time to monitor your app's usage after its release, and track related threats in real-time. What are threat actors’ preferred attack vectors? How can you evolve to improve your defenses? Guardsquare’s ThreatCast can provide the answers.
 Now it’s time to monitor your app's usage after its release, and track related threats in real-time. What are threat actors’ preferred attack vectors? How can you evolve to improve your defenses? Guardsquare’s ThreatCast can provide the answers.
Now it’s time to monitor your app's usage after its release, and track related threats in real-time. What are threat actors’ preferred attack vectors? How can you evolve to improve your defenses? Guardsquare’s ThreatCast can provide the answers.