Using Protection Report to Improve Your Security Posture
In the process of mobile app development, maintaining robust security is pivotal. A dashboard within a protection tool that assesses the app's security posture can offer significant value. This central interface shouldn't merely present the security metrics but interpret them, offering an at-a-glance understanding of the app's vulnerabilities and strengths. More critically, such a dashboard should transcend traditional passive reporting by providing actionable configuration advice. Apart from alerting developers of weak points in their app protection, it should actively steer them towards solutions, ensuring the app isn't just secure in its present state but remains resilient against future threats. In essence, by integrating the app security posture assessment with analysis and guidance, this dashboard becomes the keystone in a strategy that champions proactive, informed, and adaptive security measures for mobile apps.
How do you use a security protection report to improve your mobile app's code security?
A mobile app developer can benefit immensely from a report that outlines the current security posture of their mobile application in many ways:
- Instant visibility: A dashboard offers a consolidated visual representation of the app's protection status. Instead of combing through lines of logs or data, developers can instantly grasp areas of the code where applying protection will be impactful, allowing room for improvement.
- Trend analysis: Developers can identify recurring or unexpected issues, understand the efficacy of applied fixes, and preemptively address potential vulnerabilities.
- Compliance adherence: For apps in regulated industries, ensuring compliance with industry standards and regulations is crucial. Even in non-regulated industries, there is a need to adhere to internal processes, such as complying with the security team's requirements. A dashboard can highlight areas where the app might fall short, helping avoid potential legal and financial ramifications.
- User trust: An app that prioritizes security fosters greater user trust. By routinely checking and acting upon the insights from a security dashboard, developers can ensure their user base remains confident in the app's integrity.
- Optimized protection tool configuration: The information from the dashboard isn't just diagnostic; it's prescriptive. By understanding the coverage of the protection techniques applied, developers can better configure the mobile application protection tool. For instance, if the dashboard highlights certain protection techniques like obfuscation or encryption that have not yet been applied, developers can make an informed decision on whether implementing them makes more sense in order to improve the security posture.
- Educational insights: A comprehensive dashboard can be educational for developers who aren't security experts. Over time, by consistently referring to the dashboard, developers can cultivate a more refined sense of security, best practices, and potential threats.
- Cost efficiency: Before allocating resources for pentests, developers can check for any simple misconfigurations; identifying them early can prevent the need for repeat pentests after making configuration updates.
In essence, a security dashboard or report acts as both a shield and a guide. It protects the app and its users by providing insights, and it guides developers in leveraging protection tools to their fullest potential, ensuring the application remains potent against evolving threats.
Guardsquare’s Protection Report: Key elements
Guardsquare’s tools, DexGuard (Android) and iXGuard (iOS), automatically produce a Protection Report when processing an application or SDK. This report allows developers and application security officers to verify the protections in place and make necessary enhancements. The Protection Report comprises three key elements:
- Code hardening assessment that grades the app's protection based on five prominent and impactful risk categories (discussed in more detail below).
- A feature discovery section that enumerates potential features to bolster overall mobile app security.
- Tailored configuration recommendations suited for your specific application or SDK.
The Protection Report helps development teams validate their implementation of DexGuard and iXGuard's security capabilities early in the development lifecycle, driving continuous security assurance for mobile apps.
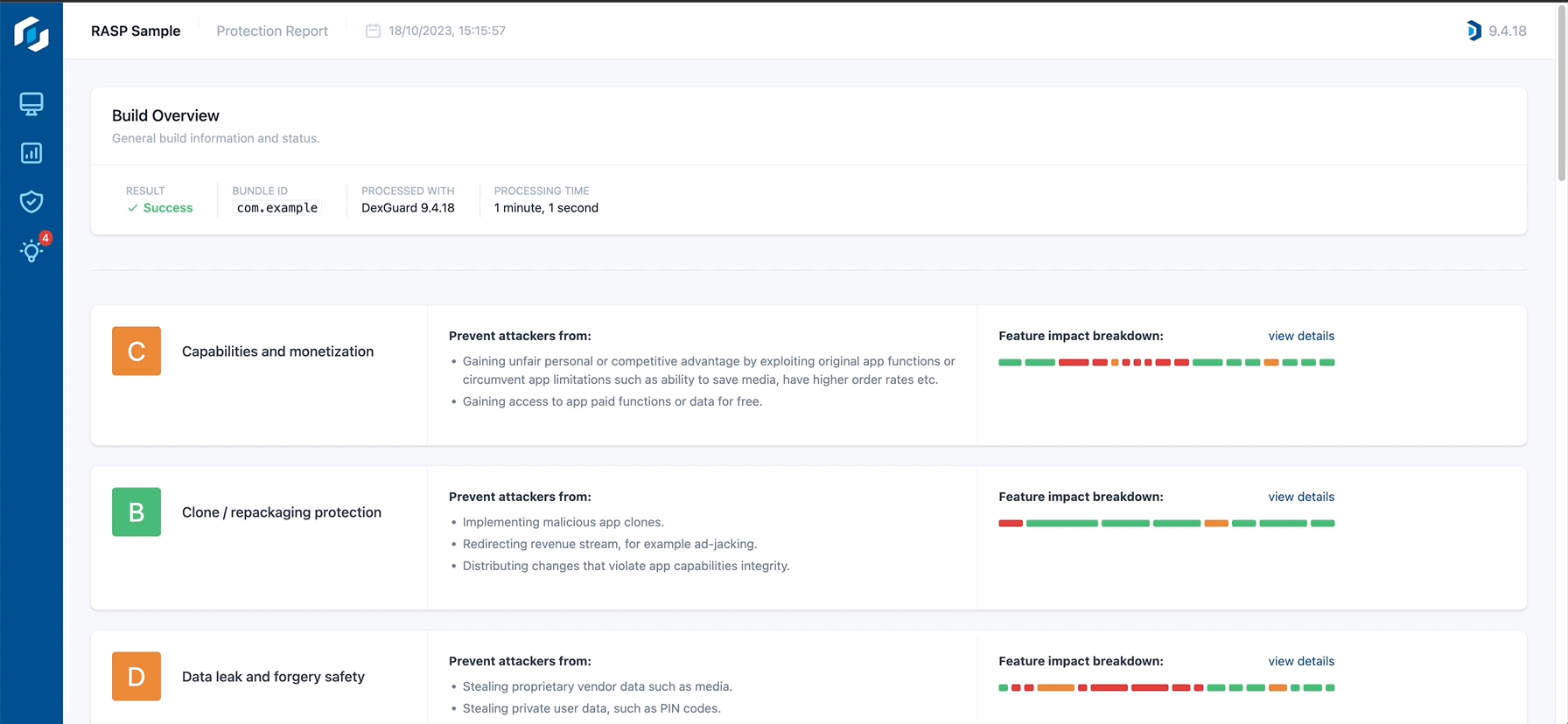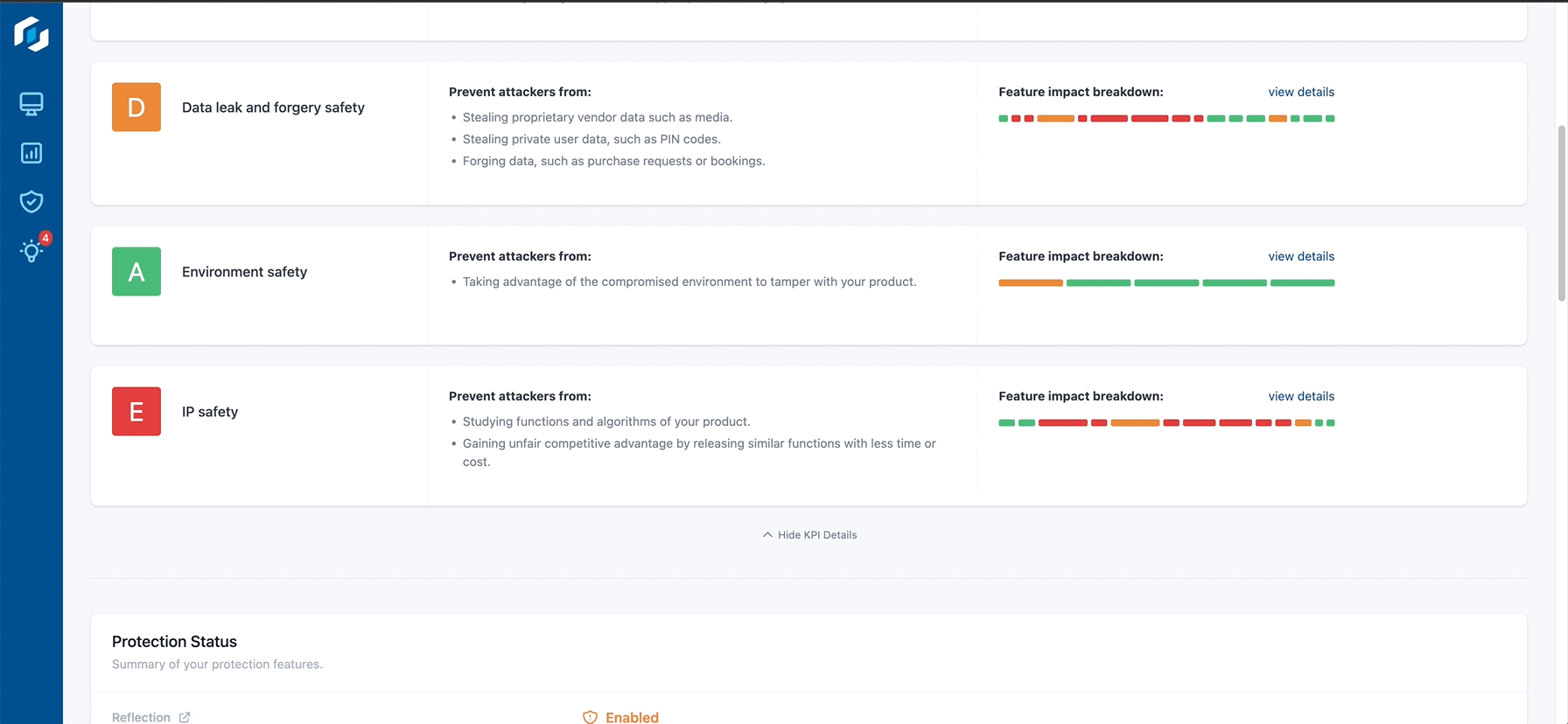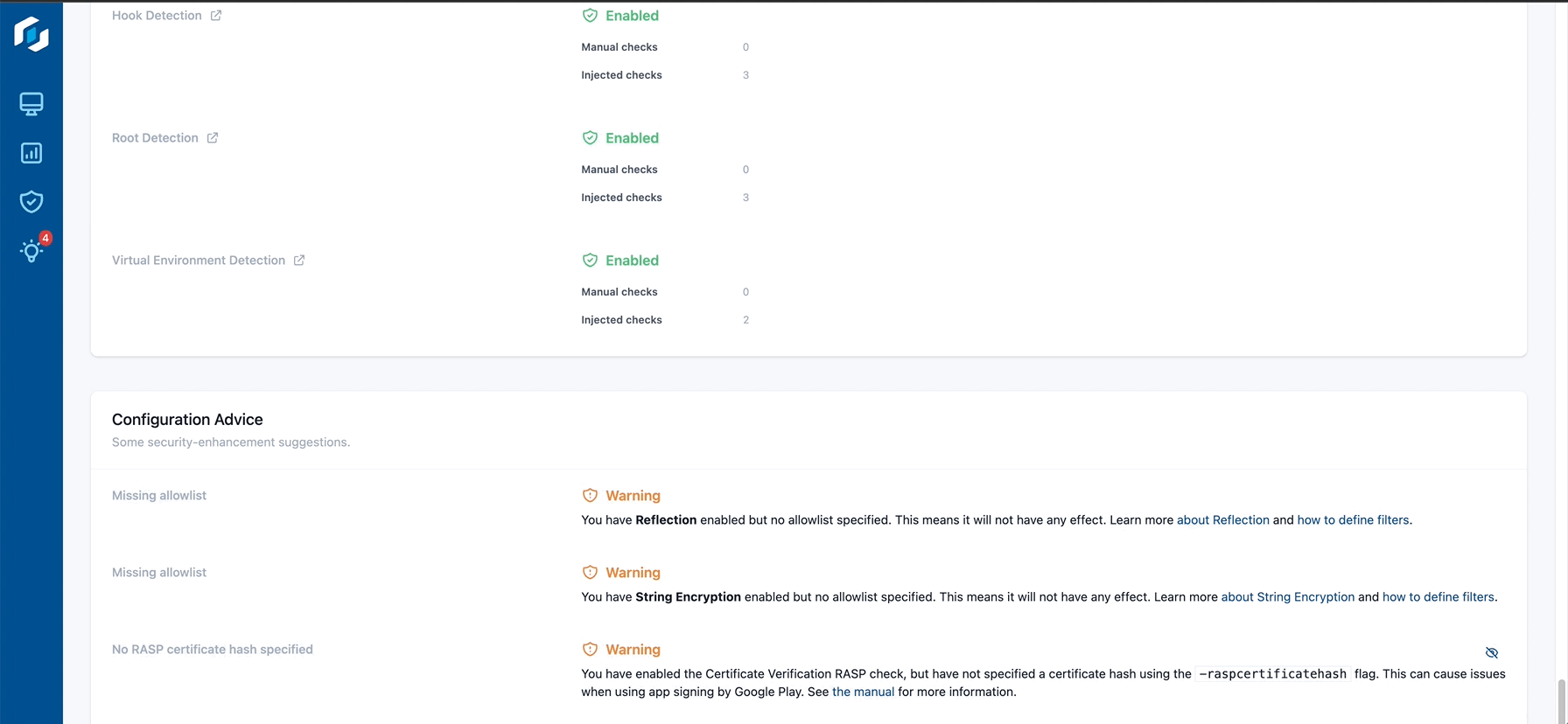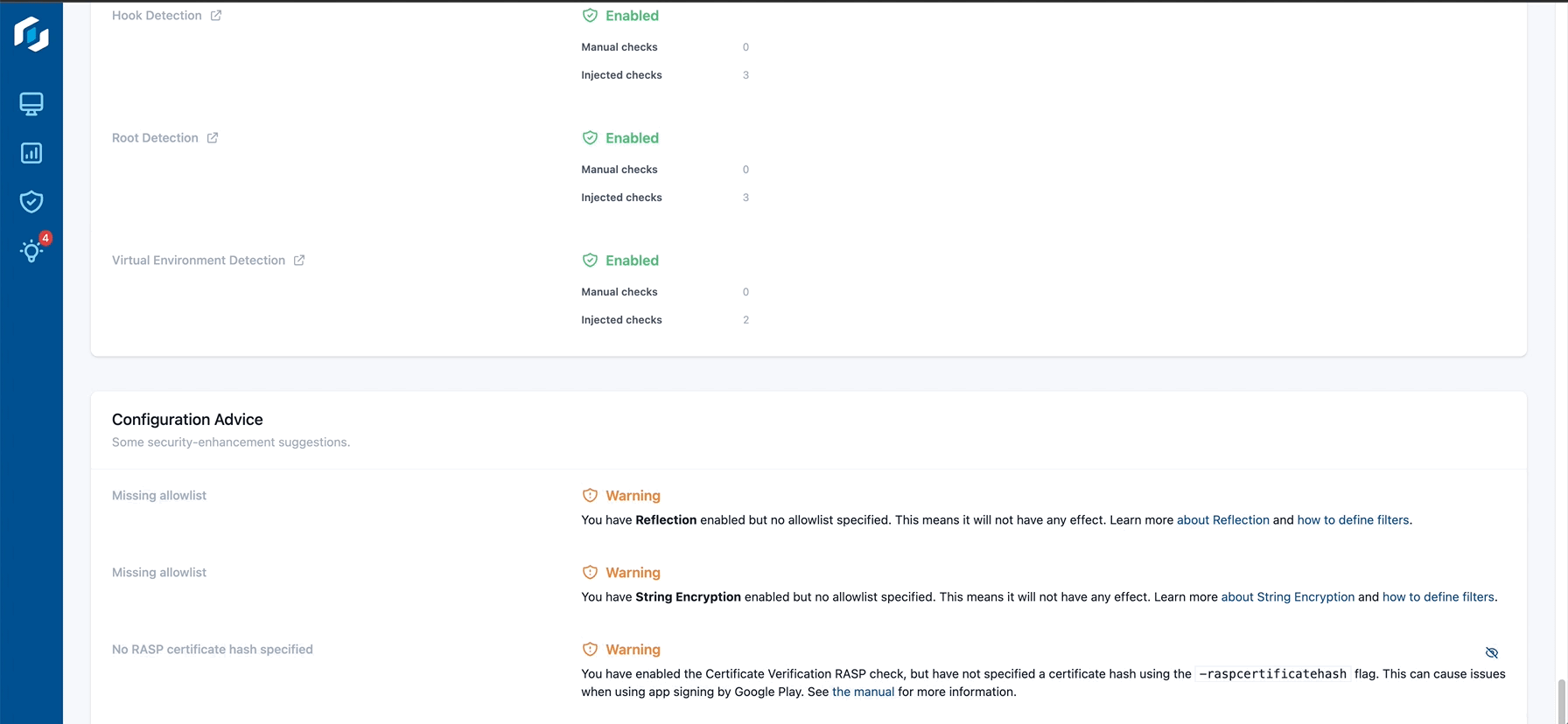
Hardening assessment
Hardening assessments enable development teams to evaluate the efficacy of their protection measures in addressing the primary threats outlined in their threat model. This assessment rates the existing protection configuration based on its effectiveness in five critical risk domains:
- Capabilities and Monetization Protection
- Cloning and Repackaging Defense
- Safeguarding against Data Leaks and Forgeries
- Environmental Security
- Intellectual Property (IP) Preservation
For each domain, Guardsquare’s Protection Report provides recommendations on optimizing the protective measures in place.
The hardening assessment scores are a guiding reference reflecting the strength of the applied code obfuscation techniques and Runtime Application Self Protection (RASP). This becomes a valuable asset for development teams to understand the level of protection that has been applied and areas where they could still be enhanced.
Assessment categories:- Capability & Monetization Protection: This focuses on the unintended addition of functionalities to applications or SDKs and unauthorized access to premium content or features.
Examples:
- Circumventing features in a secure chat app to save images meant to be ephemeral.
- Bypassing restrictions to access premium content in a game.
- Cloning/repackaging protection: Addresses the dangers of creating unauthorized replicas or modifications of existing apps.
Examples:
- Replicating a financial app with tweaks to misappropriate user data.
- Altering apps to redirect ad revenues illicitly.
- Data integrity & security: Concerns or risks associated with API security, unauthorized data access, and data forgery.
Examples:
- Extracting copyrighted media from entertainment apps.
- Intercepting confidential details, like PINs, from banking apps.
- Fabricating data such as counterfeit booking requests.
- Environment safety: Covers the risks of operating apps within potentially insecure or compromised settings.
Example:
- Using a contactless payment app on a jailbroken device risks data breaches.
- Intellectual property (IP) safety: Encompasses threats related to intellectual property theft or analysis, ranging from algorithms to complete applications.
Examples:
- Reproducing a proprietary app to introduce a rival product with minimal costs quickly.
- Scrutinizing an e-commerce site's process flow to integrate it into a generic aggregator application.
Make sure you are using all the latest product capabilities
In addition to hardening assessment, the Guardsquare Protection Report provides a comprehensive overview of potential code hardening and RASP measures that you can activate to improve the security of your application or SDK.
The Protection Report also meticulously enumerates the features that development teams can employ to enhance the security framework of their application or SDK. The Feature Discovery Component is an invaluable asset for identifying both underutilized features and recently introduced capabilities in DexGuard and iXGuard. This component helps you keep abreast of the dynamic threat landscape and fully harness Guardsquare's robust protection offering to ensure optimal safeguarding of your mobile assets.
Tailored configuration advice
Guardsquare's Protection Report meticulously examines your DexGuard and iXGuard configurations, identifying possible misconfigurations and highlighting areas for improvement. Tailored to your specific application or SDK, the report offers insightful configuration advice.
This guidance, drawn from the collective expertise of our security research team, is designed to optimize DexGuard and iXGuard's multi-layered defenses for your unique use-case scenarios.
Protect, test, monitor, repeat
Guardsquare's Protection Report empowers development teams to promptly verify the integration of DexGuard and iXGuard's security features, helping to reduce the risk of costly and time-consuming security breaches. Addressing potential security issues early in the development lifecycle streamlines the testing and implementation process, saving teams valuable time and resources. This ensures that applications or SDKs consistently safeguard against prevalent mobile app security threats, such as reverse engineering, IP theft, fraudulent app clones, and sensitive data loss.
Paired with real-time threat data from ThreatCast, Guardsquare’s monitoring platform, the Protection Report offers a comprehensive view of application security, helping teams stay ahead of the evolving threat landscape and identify and respond to new threats quickly and effectively. The Protection report is complementary to Guardsquare’s MAST product, AppSweep, which can scan Android and iOS apps at any point of the app lifecycle (also after publishing) to provide developers actionable recommendations for quickly and effectively addressing security issues in the app's code and dependencies. AppSweep’s automated mobile application security testing typically uses software tools that employ one or more techniques to analyze the software to detect potential vulnerabilities throughout the SDLC. Guardsquare’s Protection Report, on the other hand, provides developers with a resource to optimize the application of the various protection techniques in DexGuard and iXGuard for mobile applications.




