5 Lessons Learned After 1 Year of Mobile App Security Testing

Summary
There has historically been a trade off between mobile app security and getting a functional app to market. With mobile apps now the primary channel to reach customers, overlooking security can come at a huge price
Consider, for example, that the average cost of a data breach has reached an all-time high of $4.35M in 2022, 12.7% more costly than in 2020. And data leaks happen on mobile apps, too. According to recent research, over 1,800 Android and iOS apps have been found leaking hard-coded AWS credentials. Such credentials are typically used to access app resources or backend systems where sensitive data might be stored, like IP or personal identifiable information (PII). Those are low-hanging fruits for cybercriminals willing to profit from reverse-engineering and tampering with weak mobile apps.
Clearly, the tradeoff between mobile app security and time to market is one that organizations just cannot risk in today’s mobile-first world. We set out to solve for this app security + development gap with the launch of AppSweep, a free, developer-friendly mobile application security testing tool. With AppSweep, developers can more easily find and fix issues early in the software development cycle.
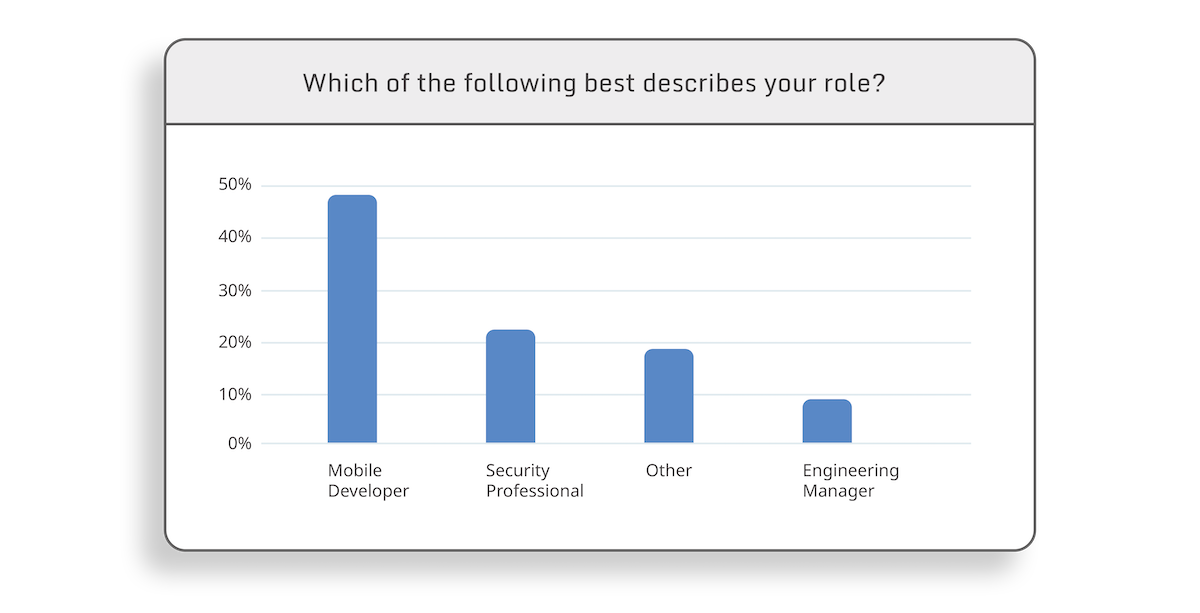
In the first full year AppSweep has been available, we learned a number of things. For example, developers want to use security checks, they just need to have the right tool. We also observed that it wasn't just mobile app developers (across all sectors) using AppSweep, but also team leads, engineering managers and security professionals that leaned into the insights and proactive recommendations AppSweep provides.
To truly understand the implications of the top five lessons we’ve learned in the past year as it relates to mobile app security testing, let’s explore some of the key elements that led to the creation of AppSweep.
The challenges with mobile app security testing
When our AppSweep journey started, we knew we faced a challenging task: We wanted to create a mobile application security testing tool that would resonate with teams of mobile application developers who are increasingly aware of security, but remain reluctant to incorporate it in their routines.
After all, even though security should start “left” with the developers, the reality is that they are notoriously skeptical of processes that are seen as inefficient or disruptive to getting software released. And that’s for good reason: When you have to push features every week and ship them in production, the last thing you want as a mobile app developer is to be slowed down by additional, non-strictly coding tasks given to you without actionable recommendations.
The answer: an automated tool that could scan an entire app within minutes, without sending development teams on a goose chase. Basically, we wanted to quickly provide developers with clear insight so they can better understand security vulnerabilities and weaknesses in their app.
We also knew that mobile developers want a familiar experience, one that translates to a tool that speaks their language (code snippets, yes please!) and incorporates actionable recommendations.
Now, thousands of AppSweep builds later, we are ready to share with you the highlights of what we have learned.
Lessons learned with AppSweep
1. Teams check their app security posture on a regular basis (with the right tools)
According to a survey we conducted among AppSweep users over the past several months, developer teams are more likely to scan their apps for security vulnerabilities at least each build / commit when compared to those who test their application only once.
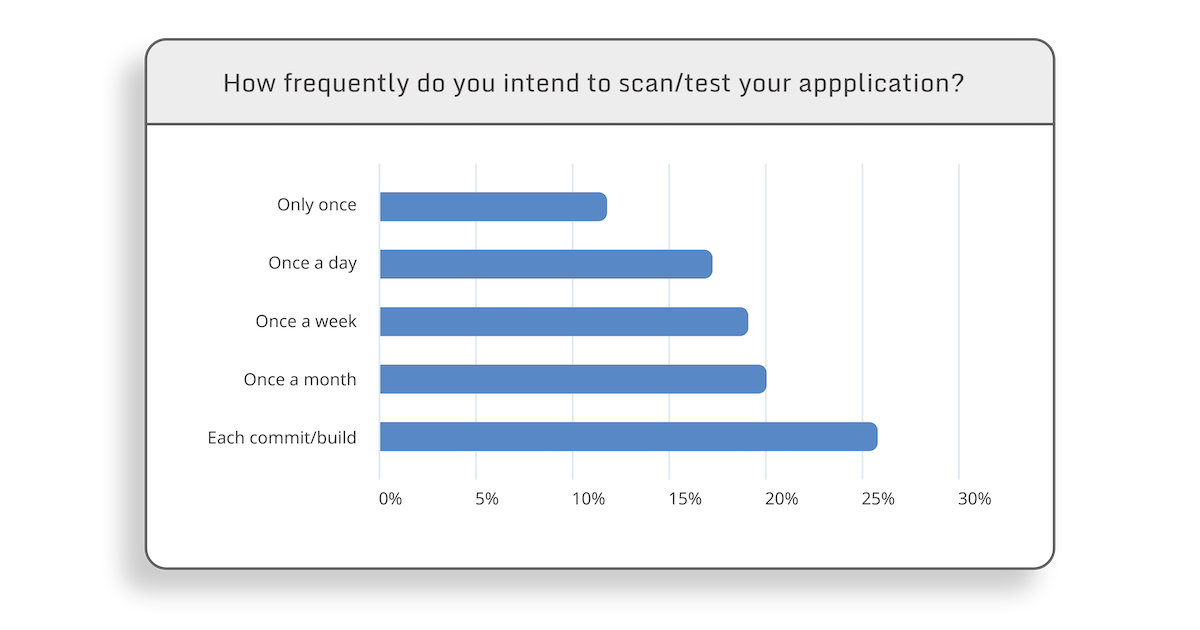 In order to achieve that goal, mobile app developers need a non intrusive tool that reconciles their need (and pace) to push features for their end users with quick and easy security fixes. And in the case of complex mobile apps where development involves more than one team, this provides developers with a more streamlined way to be on the same page, security wise, when they are ready to commit.
In order to achieve that goal, mobile app developers need a non intrusive tool that reconciles their need (and pace) to push features for their end users with quick and easy security fixes. And in the case of complex mobile apps where development involves more than one team, this provides developers with a more streamlined way to be on the same page, security wise, when they are ready to commit.
With this in mind, we provided a “project sharing” link in the mobile application security testing tool, as well as a “compare diff” view at project level, rather than gating the developers´ commit if a scan fails a certain threshold. Doing so enables all team members to be notified if new vulnerabilities are detected in a scan.
Sharing is caring, and security testing works best if it becomes a shared responsibility.
2. Mobile developers use security tools that are easily demonstrated and proven with helpful tutorials
We developed AppSweep following familiar concepts for developers, like the ones they have in their IDE’s: dependencies in the code, package hierarchy, class structure.
But even with an intuitive, easy-to-use tool like AppSweep, we received an overwhelming response when we dropped this tutorial in cooperation with security enthusiast and code instructor Philip Lackner.
And to tell the truth, that was a bit of a no-brainer; tutorials allow you to put your newly-acquired knowledge straight to use. That kind of “hands-on,” pragmatic (but also interactive) mentality is at the core of developer teams’ best practices.
In our case, developers mostly appreciated the practical insight of being shown, within minutes, how to integrate the tools into their pipelines. That brings us to lesson #3
3. Smart tech leaders integrate security checks in their CI/CD pipeline
We observed that teams who integrate their AppSweep scans in their pipelines are more likely to regularly fix vulnerabilities. Efficiency gains are the ground truth behind this lesson, so why spend time manually pushing scans when you can automate it?
Of course, getting your team to automate their scans requires an integration option that makes sense and is easy to use. That is why we decided to focus initially on a Gradle Plugin. This is the easiest way to include AppSweep in your process since Gradle is widely used by developers as part of Android Studio, so scans could be performed without leaving the IDE. Once integrated, Gradle also provides lots of additional context that allows the tool to detect dependencies in the code better.
We didn’t stop at the IDE though; we leveraged the Gradle Plugin to be used in a variety of CI/CD tools, including (but not limited to) Bitrise, Jenkins, GitHub Actions, etc..
If you are interested in gaining deeper knowledge on how to integrate AppSweep in your CI/CD pipeline, read more here.
4. Security professionals benefit from mobile application security testing tools too
Though AppSweep’s initial primary target following launch was mobile developers, we noticed that security teams use it regularly, as well.
 Specifically, they appreciate how AppSweep's mobile app analysis can help with the automated detection of a number of Mobile Application Security Verification Standard (MASVS) violations defined in the OWASP Mobile Security Testing Guide (MSTG). Issues are grouped according to key categories that help security professionals filter them and quickly understand to what extent their apps are compliant with OWASP standards.
Specifically, they appreciate how AppSweep's mobile app analysis can help with the automated detection of a number of Mobile Application Security Verification Standard (MASVS) violations defined in the OWASP Mobile Security Testing Guide (MSTG). Issues are grouped according to key categories that help security professionals filter them and quickly understand to what extent their apps are compliant with OWASP standards.
Another benefit for security professionals is the streamlined communication option to have PDF reports regularly pushed to their compliance departments.
That comes as no surprise, given the fact that security professionals make use of mobile application security testing as a “surveillance tool” and extract best practices from it to disseminate across the company.
All in all, the key takeaway here is that mobile application security testing tools that provide extra functionality, like compliance with OWASP mobile app security standards and the generation of security overview reports, are adopted and appreciated by security teams. These insights minimize the need to have multiple security tools in the company.
5. Mobile app developers like advanced analysis to tailor testing to their unique needs
We recently made available the possibility for our users to switch on advanced analysis for improved vulnerability detection in projects. Advanced analysis enables additional findings like:
- Detection of user input flowing into class loaders or interpreters.
- Detection of sensitive user data being written to disk/ to IPC mechanism/ to logs.
- Detection of sensitive information written into a notification.
- Detection of sensitive user data being sent to the Internet.
- Detection of insecure passwords for the certificate keystores.
Whether it is faster scan time or proactive recommendations for addressing findings, developers appreciate the chance of being in the driver's seat when it comes to security checks.
So far, we have shared lessons from AppSweep’s past. Now it is time to look into its future!
What's next for Guardsquare with mobile app security testing?
As we celebrate the one-year mark with AppSweep, you might be wondering what’s next. We have a few plans on the radar, including:
- iOS - we are planning initial support for iOS apps, to bring all the benefits we’ve achieved with Android to iOS mobile developers
- Greater adoption - you’ll see this in our efforts to integrate our help articles into an AppSweep online chat. We’re doing this so we can help you at the very moment you need it: while you are using the app, reducing the need to spend time searching and filtering!
- Increasing OWASP coverage - we will continue to uncover additional actionable findings to present, covering more of the OWASP Mobile Application Security (MAS) project through automated security tests.
Throughout AppSweep's evolution, Guardsquare is committed to making mobile app security testing accessible for developers and security teams, with few barriers to adoption. We believe mobile app security should be a constant in everyone's development process, regardless of whether you are a small startup, or a scaled enterprise.




