OWASP MASVS Recommendations For Reinforced Mobile App Security

This blog explores:
- OWASP is a valuable security resource that should not be overlooked, as it enables developers to leverage the knowledge of a global community of security experts through frameworks with focused and actionable mobile app security recommendations.
- Based on OWASP’s common mobile threat list and recommendations, it’s not enough to approach security on an as-needed basis; it must be part of the overall development strategy. Developers need a complete suite of security solutions that protect, test, and monitor apps.
- With a full suite of mobile app security solutions, developers can protect apps with code hardening techniques, test their app’s security posture throughout the SDLC, and monitor for threats to catch attackers before they can cause real damage.
There are more mobile app security myths circulating today than you may think. One that stands above the rest is that mobile operating systems provide adequate security protection on their own. The OWASP MASVS, or the Open Worldwide Application Security Project Mobile Application Security Verification Standard, is the industry standard for mobile app security. The OWASP MASVS framework is used to define requirements and provide security controls for both app developers and security testers.
The reality is that mobile operating systems cannot protect your apps from threat actors who leverage various attack methods, like reverse engineering and code tampering, to infiltrate your app.
This at a time when mobile apps are a growing focus for threat actors. Brand abuse attacks (fraudulent clones and IP theft) across Android and iOS apps increased by 274% in 2021. With private data, IP theft, brand reputation, and customer trust on the line, developers need a way to protect their apps beyond mobile operating systems.
Do I need mobile app security?
Another myth that could hurt your mobile app security posture is the belief that mobile app security is only necessary for regulated industries. In reality, threat actors are active across regulated and unregulated industries.
In fact, 45% of apps across all industries have high-risk issues, and 35% have critical issues. These vulnerabilities must be addressed, especially when you consider that 70% of mobile app users say they would stop using an app and switch to a competitor due to security concerns.
There’s clearly a need for dedicated mobile app security. But where do you start? Let’s take a look at what OWASP is and how you can leverage its Mobile Application Security Verification Standard (MASVS).
What is OWASP and how does it help?
OWASP is an online community that provides free mobile app security articles, documentation, and tools (among other resources). The OWASP community is built on the collective knowledge of cybersecurity experts around the globe, effectively translating mobile app security requirements and best practices into actionable recommendations to help developers address regularly emerging new threats and vulnerabilities. It also shares reliable frameworks to help identify and remediate mobile app vulnerabilities.
The MASVS framework
A great example of an OWASP framework is the Mobile App Security Verification Standard (MASVS). This framework provides a model to think about the security requirements for your mobile application. The model consists of three layers: standard security (MASVS-L1), defense-in-depth (MASVS-L2), and resiliency against reverse engineering and tampering (MASVS-R).
Mobile Application Security Verification Standard
(MASVS Layered model)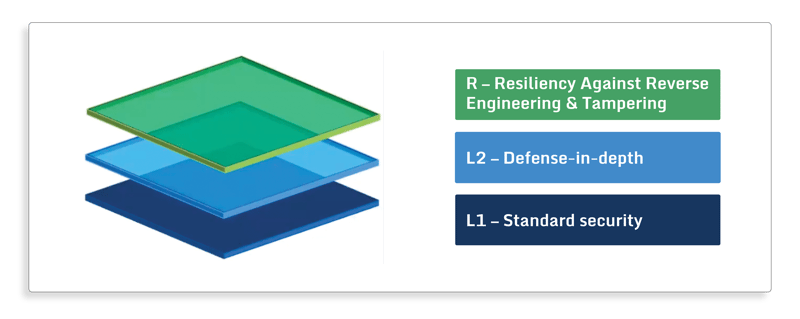
The first layer (MASVS-L1) provides a general set of recommendations that should be adopted by all mobile apps. Implementing these will result in a secure app that will not suffer from common vulnerabilities.
The second layer (MASVS-L2) provides defense in depth controls, such as SSL pinning. Implementing the recommendations of the second layer will fortify your app against more sophisticated attacks and keep your sensitive data safe.
The third layer (MASVS-R) encompasses very strict controls to prevent reverse engineering and code tampering, which can be used to thwart security measures implemented in the app.
To make all of this more manageable as you get started, OWASP provides a Mobile Top Ten, which is a list of the most commonly found security risks in a mobile app environment.
OWASP Mobile Top Ten List
The OWASP Mobile Top Ten provides a strong foundation for building a better mobile app security program, outlining the key issues a development team should focus on. To take a deeper dive into the OWASP Mobile Top Ten, check out our report The OWASP Mobile Top 10 List and Why it Matters for App Developers.
Top 10 categories of mobile threats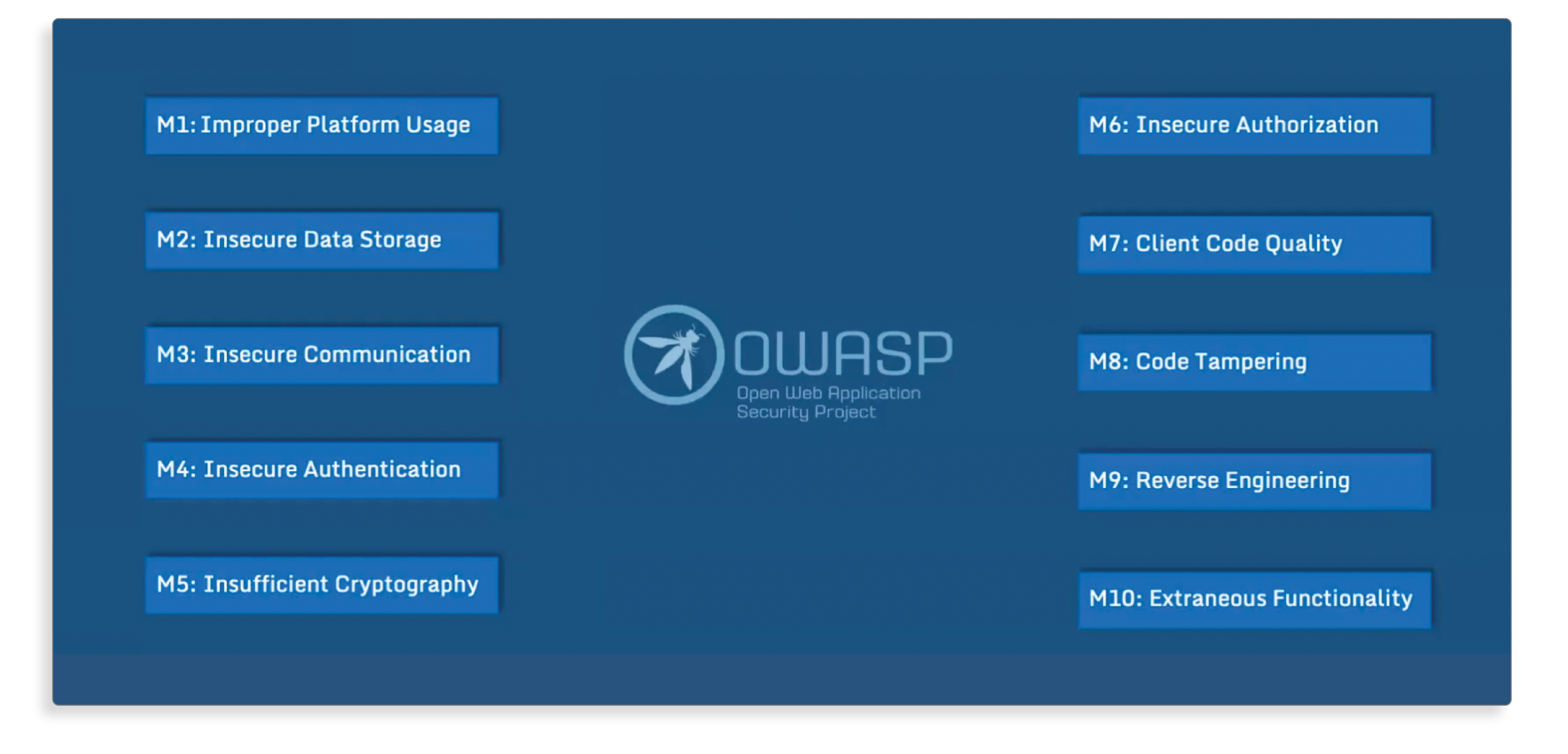
Let’s explore how you can map the recommendations of OWASP’s mobile app security framework to the threats listed above to better secure your app.
How to act on OWASP’s Mobile Application Security Verification Standards
Based on the variety of OWASP’s Mobile Top Ten List and its framework recommendations, we can see that it’s not enough to approach security on an as-needed basis — it must be part of the overall development strategy. Developers need a complete suite of security solutions that protect, test, and monitor apps throughout the entire software development lifecycle (SDLC).
Developers can achieve these objectives by splitting up their mobile app security process into two parts.
Part 1 - OWASP MASVS Best Practices
The first part focuses on what developers should do outside of actual code development. This includes developing a threat model to understand how your app might be attacked and for what purposes. Then, developers can focus on adopting key security best practices as part of the software development process as a whole.
Part 2 - OWASP MASVS During Development
The second part focuses on what developers should actually implement during the mobile app development process.
Protect
Core to a solid mobile app security strategy is a strong code hardening solution to thwart attackers from using reverse engineering to gain insights into the operation of your application and exposing potential vulnerabilities. Effective options will include techniques like obfuscation and encryption. Solutions that also support polymorphism (where the obfuscation and encryption changes with each build) offer a higher level of protection.
Test
A mobile app security testing solution should be fully integrated into the SDLC. As a development team, you want to know about security vulnerabilities as soon as possible to quickly mitigate them during development before they cause a major issue post-release.
Monitor
Last but not least, you need to have a solution to monitor the application once it is released and running on the end user's mobile device. A threat monitoring solution will enable you to identify suspicious users, find security gaps that need patching, and gather expert security knowledge for future rounds of development.
With a full suite of mobile app security solutions, developers can protect apps with code hardening techniques, test their app’s security posture throughout the SDLC, and monitor for threats to catch attackers before they can cause real damage.
Find a solution that’s right for you
You cannot address all of OWASP’s MASVS recommendations without a solution that includes protection, testing and monitoring to defend against mobile app threats like reverse engineering, static and dynamic analysis, code tampering, and API abuse.
DexGuard and iXGuard, provide code hardening using obfuscation and encryption techniques for your app’s classes, fields, arithmetic instructions, and a variety of other security features such as code virtualization and API call hiding. The protection DexGuard and iXGuard offer is also polymorphic. Each app build has a different obfuscation configuration, preventing an attacker from using prior knowledge.
For mobile app testing, a solution like AppSweep enables developers to gain fast, accurate, and actionable feedback to efficiently and effectively improve the security posture of their mobile app during development.
To monitor your app’s security after release, ThreatCast enables developers to view suspicious activity as it occurs. You can drill down into specific events to analyze threat actors’ attempts at reverse engineering and tampering to identify common attack vectors. You can also set up customized alarms to alert yourself to threat events in real-time and respond before a breach occurs.
To learn even more about OWASP’s mobile security framework and gain practical recommendations for developing secure mobile apps, check out our report The OWASP Mobile Top 10 List and Why it Matters for App Developers.





