Threat Monitoring: Your Mobile App Security Secret Weapon

A centralized security information and event management (SIEM) platform is a common tool that has been widely adopted by organizations across industries to mitigate cybersecurity risks and meet regulatory compliance standards. Unfortunately, the real-time collection and utilization of mobile applications’ threat-specific data often remains a blind spot.
Mobile app threat monitoring can — and should — provide far greater value than simply displaying threats apps are facing in real time. On top of providing contextual information about the types of attacks and threat actors themselves, such tools can guide an organization’s ongoing mobile app development and security strategy.
In this blog, we will explore the features and capabilities of ThreatCast, Guardsquare’s real-time threat-monitoring product.
Gain deeper, contextual insights into your threats with ThreatCast
After you have activated runtime application self-protection (RASP) checks and added your ThreatCast API key to your DexGuard and iXGuard configurations, ThreatCast can immediately start providing you insights into suspicious app users and behaviors in deployment. It does this by monitoring your applications for any RASP checks triggered during integrity violation attempts and reporting them via the ThreatCast dashboard in real time.
“ThreatCast has helped us stay on top of the different kinds of threats our apps are facing. The breadth and depth of real-time data ThreatCast collects is impressive. We can now pinpoint users with suspicious activities along with their device and location information to take the necessary measures whenever required." - CTO, Emerging social media platform
Three categories of ThreatCast alerts
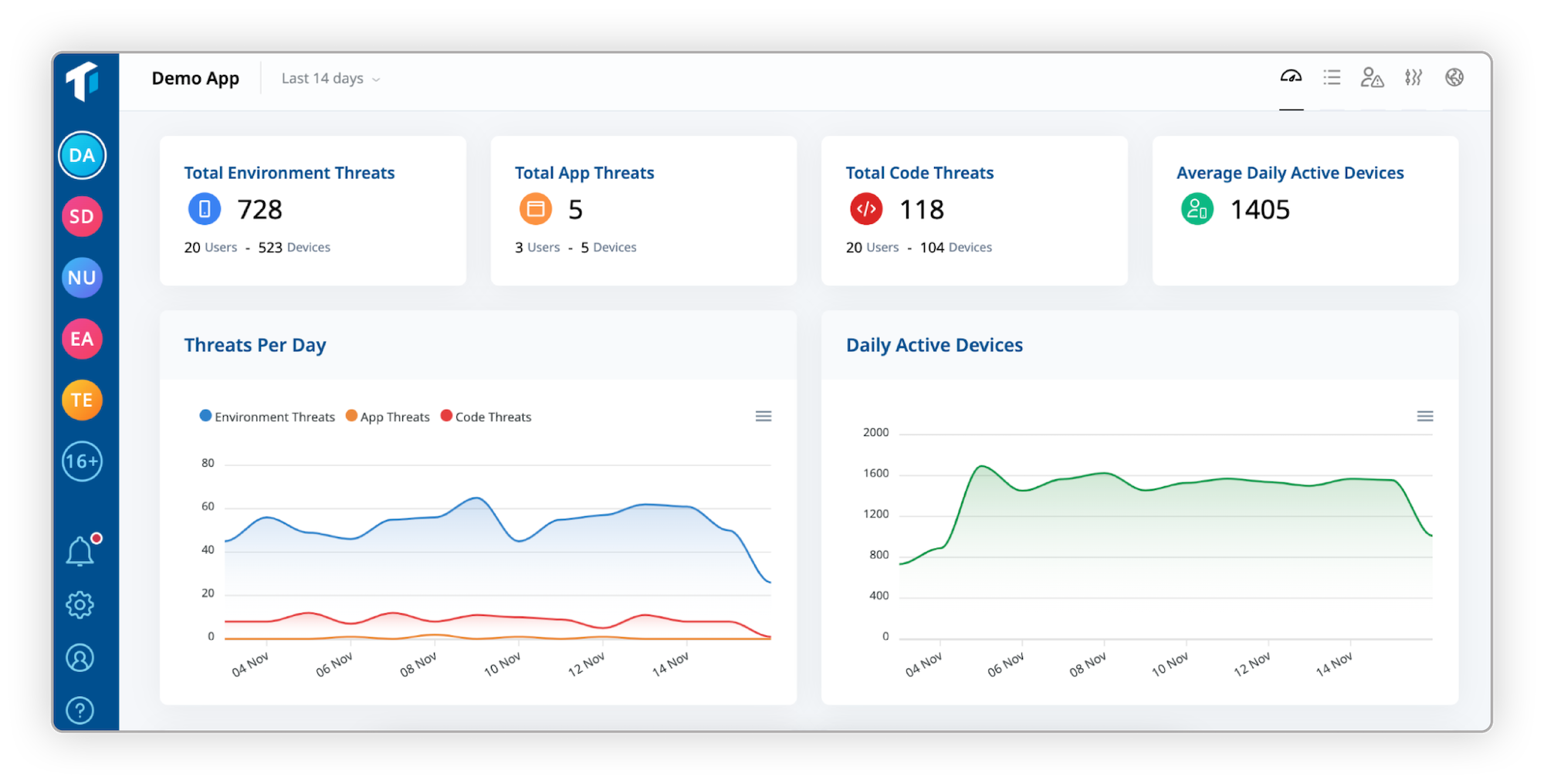
ThreatCast categorizes the observed threats into three distinct categories: environment, app, and code threats.
#1 Environment threat
An environment threat is triggered whenever an end-user attempts to run your mobile app in a potentially insecure or risky environment. Although this type of attack does not necessarily indicate malicious activity, it often serves as the foundation for further attacks.
A few examples of environment threats include:
- The app is running on a rooted or jailbroken device.
- The app is executed in some sort of emulator.
- The app detects that there is a debugger or other reverse engineering tools attached to the end-user’s device. This indicates an imminent threat as this means that the user is in the process of attacking the app.
#2 App threat
An app threat is triggered whenever an end-user attempts to compromise or modify your app's binary. These threats are considered to be more serious than environment threats since this indicates the end-user has attempted to modify or tamper with the application itself.
A few examples of app threats include:
- The app has different certificates and has been resigned.
- The app loads libraries that are different from what the original app would load.
- The app is different from the original app and has been repackaged, which means threat actors successfully executed their attack and potentially distributed a modified version of your app to the public.
#3 Code threat
A code threat is triggered when an end-user attempts to statically or dynamically alter the internal logic, behavior, and functionality of the app. These threats are the clearest sign that the app is being actively attacked by the end-user.
A few examples of code threats include:
- The app contains additional code that is not part of the original app.
- The app’s function table pointers behave differently from the original code.
- The app has a function hook added, modifying the app’s runtime behavior.
Additional context provided by ThreatCast
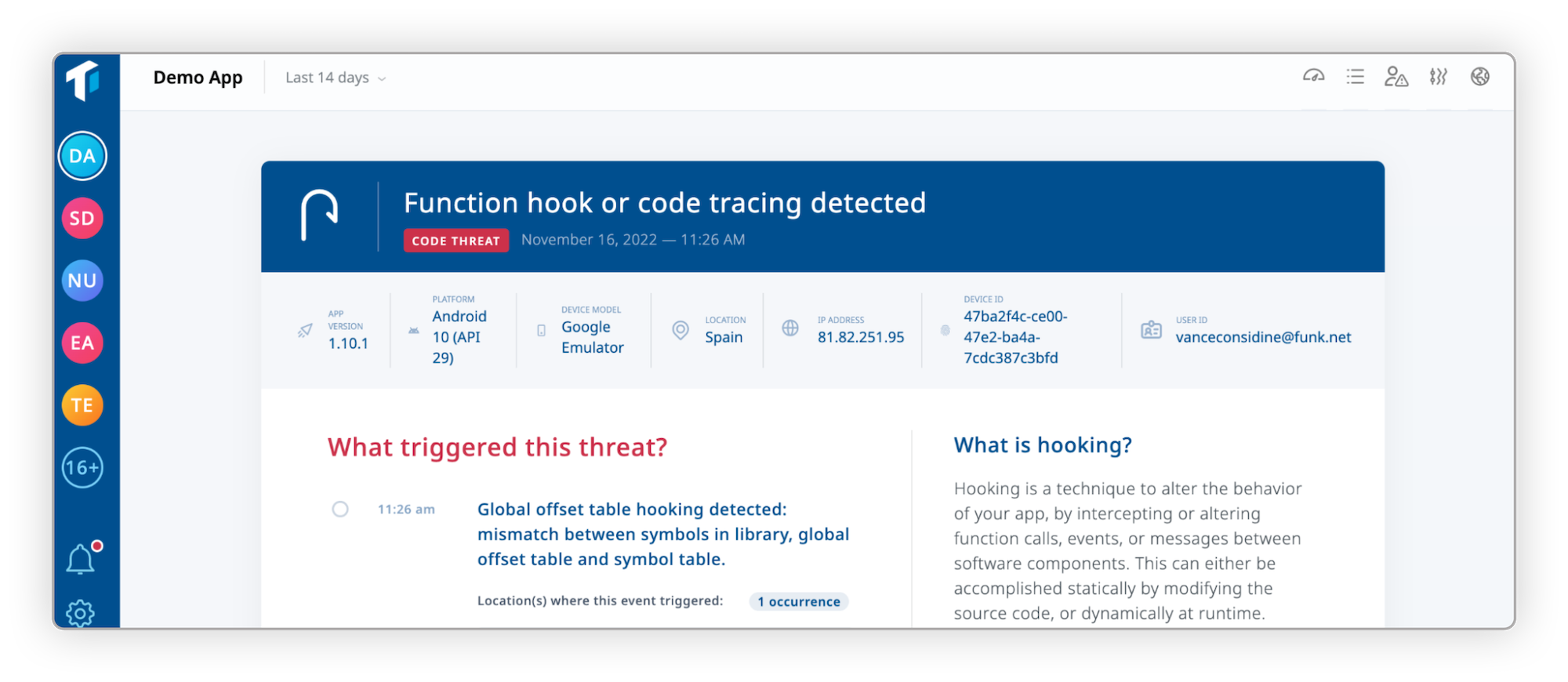
“While [the app] uses a security-hardened design, I appreciate the extra layer of security, visibility, and protection that ThreatCast provides by monitoring both the app and the device environment.” - Developer, AI tool provider
On top of being able to easily understand the severity of each threat, developers can further filter and analyze each threat alert. This can be done efficiently thanks to the wealth of contextual metadata ThreatCast collects and displays along with the threat alerts, such as:
- Type of Threat/Attack
- App User ID
- App Version
- Geolocation
- Device ID
- IP Address
- Device Model
- Platform Version
- Date and Time
- Incidence rate
By incorporating threat alerts with additional information surrounding the events, ThreatCast helps guide users to come up with actionable and concrete plans for improving their mobile app security strategies.
Making ThreatCast data work for you
“Dozens of our team members actively use ThreatCast on a daily basis. Its handy dashboard has allowed our team to gain a much deeper understanding of which part of our code is being attacked, allowing us to finetune the protection configurations our apps truly need. Additionally, we are now able to more confidently ban or block malicious users thanks to ThreatCast’s user-specific data such as UserID and DeviceID.” - Mobile Front End Lead, Southeast Asian Hypergrowth FinTech Company
Understand common threats and update protection configurations accordingly
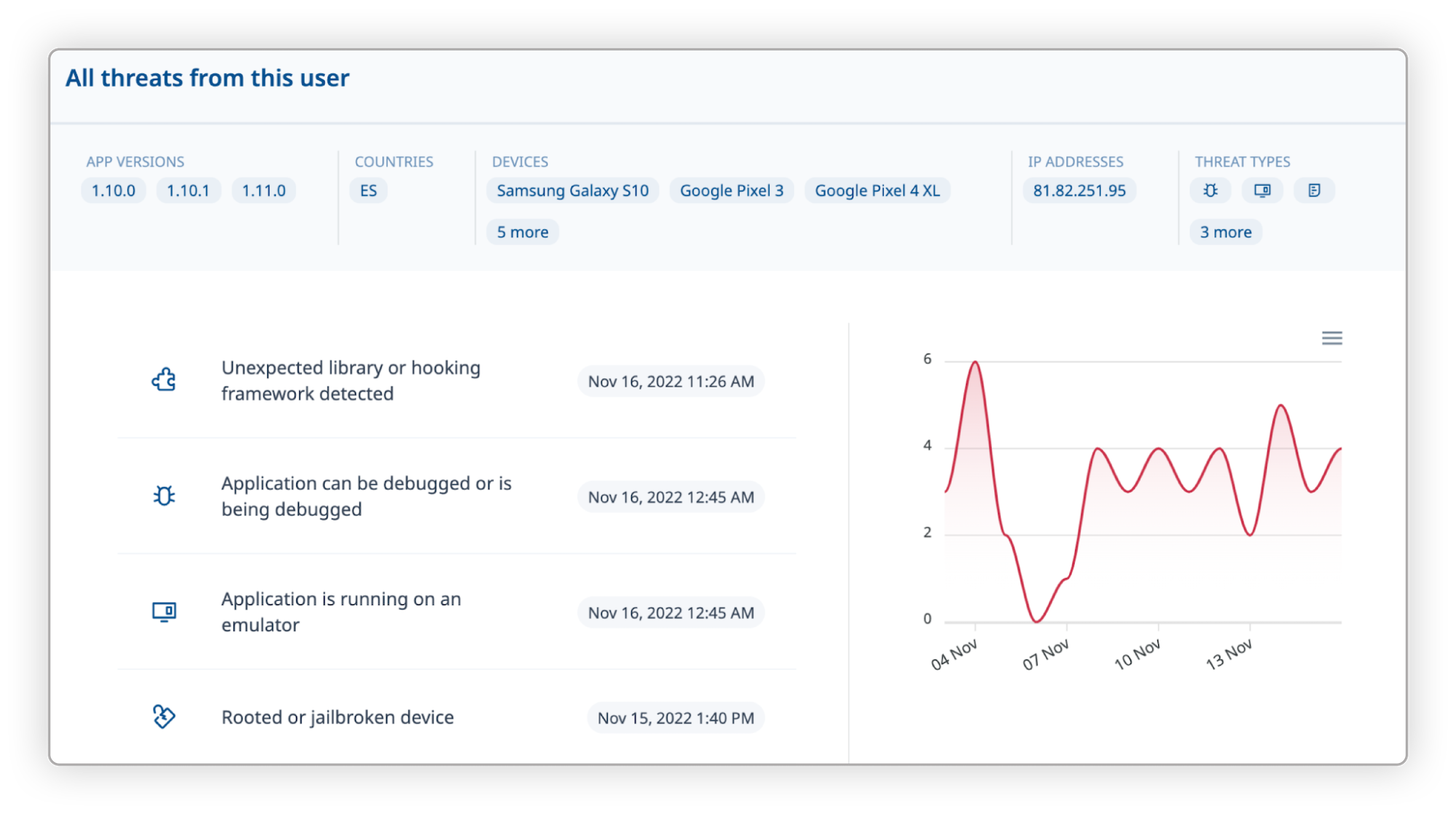
The detailed description of each detected threat allows the development and security teams to figure out which parts of the code are most frequently attacked, who the perpetrators are, and how they attempt to compromise the application's integrity. For the development team, this additional context is useful to validate the effectiveness of DexGuard and iXGuard RASP checks and finetune protection configuration and release cycles whenever necessary.
Trigger the right countermeasures
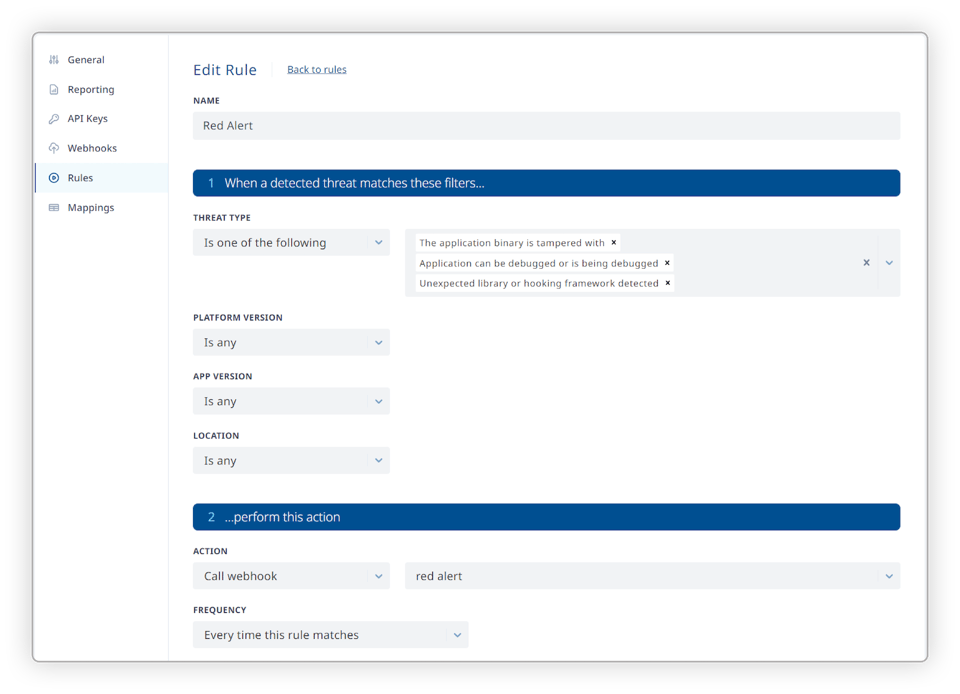
ThreatCast Business & Enterprise users have the capability to set up custom rules to filter and prioritize visibility into the most important events or spikes you care about. You also have the option to filter these results based on the contextual metadata such as platform version, app version, and the location of the app users, to create a tailored awareness whenever these occur. By utilizing this feature, the right teams are automatically notified about the most relevant threats in a timely fashion, allowing you to formulate the most suitable remediations where and when necessary.
Enrich crash and anti-fraud response
Awareness when setting up rules triggers is important, while the webhook feature brings the actionability of threat monitoring data to the next level. Combining the use of custom rules and the custom webhooks features, ThreatCast Business and Enterprise users can also seamlessly feed dynamic threat insights into their existing monitoring tools such as performance & crash analytics, SIEM, and anti-fraud systems (i.e., QRadar, Splunk).
By correlating the detected runtime integrity violations that initiate an app crash with crash log analysis tool data, ThreatCast users can gain a clear view of whether or not the app crash is caused by a bug in the app. Sharing this data with your customer support team will allow them to investigate complaints surrounding a crash more accurately, without adding work for developers.
By complementing your anti-cheat/anti-fraud strategies with real-time ThreatCast threat data, you can build more fine-grained malicious user profiles, providing you with a more solid ground for banning users or restricting their access to certain app features or capabilities.
Infusing ThreatCast data into your security strategy
"We were amazed but also taken aback when we saw the number of attack attempts our apps are facing. On average, ThreatCast reports hundreds of thousands of attack attempts that both DexGuard and iXGuard manage to prevent each month." - Information Security Expert, Top digital wallet provider.
Mobile app security professionals can leverage ThreatCast to add an extra layer of intelligence to their security strategy, informing both short-term mitigation efforts and longer-term patches and updates to the mobile app’s security architecture. These insights can also be used to guide future development projects, without negatively impacting time-to-market (TTM) or user experience (UX). As additional features and updates are released, developers can also compile threat monitoring data and compare build-over-build results to understand which releases and commits introduced new vulnerabilities.
Executive Summary (TL;DR)
- Threat monitoring can help you stay on top of the ever-evolving threat landscape, allowing you to ensure your security posture isn’t lagging behind.
- Threat monitoring can provide far greater value than simply flagging threats in real-time. It can—and should—provide broader contextual information around the types of attacks and threat actors themselves, to guide and improve your ongoing security strategy.
- ThreatCast dynamic threat insights can be seamlessly fed into existing monitoring tools such as performance & crash analytics, SIEM, and anti-fraud systems (i.e., QRadar, Splunk.)




