REPORT: The Proliferation of COVID-19 Contact Tracing Apps Exposes Significant Security Risks

Most Government-Sponsored COVID-19 Contact Tracing Apps Are Insecure & Risk Exposing Users’ Privacy and Data
The Rapid Rise of COVID-19 Contact-Tracing Apps
Since the COVID-19 crisis began, many countries, as well as public and private organizations, have rushed to develop contact tracing apps. These mobile apps are intended to help us better understand how the virus spreads—and to notify individuals if/when they come into contact with someone who has been infected. Contact tracing is part of a proven set of strategies to combat diseases such as the novel coronavirus.
However, contact tracing apps have been plagued with severe security issues from the start. Some apps, such as Qatar’s have already experienced security threats, and researchers have raised legitimate fears about users’ data being broadcast and stolen.
Yet most of the developers behind these apps are still not taking proper security precautions. When the Guardsquare team spoke with one country that had built its own contact-tracing app, they felt that they were not gathering any “data of interest,” and thus did not see the value of spending resources to improve security.
The urgency of getting these apps to market quickly is clear. The faster governments and other entities can get contact tracing tools into the hands of citizens, the better the chances of slowing the spread of COVID-19. However, it’s inadvisable to sacrifice security for speed, because there are real risks involved, which our analysis covers below.
About this report
Because these apps are so important, and because securing them and guarding user privacy is vital, Guardsquare’s team set out to understand and analyze what, if any, protections COVID-19 contact tracing apps are employing. This report summarizes our findings.
Methodology
We assessed 17 Android mobile contact tracing apps from 17 different countries. All of these apps were built by government entities (though some have used third-party contractors, which we’ll cover later).
We chose a representative sample of apps across regions including Europe, Asia-Pacific, the Middle East, and the Americas. This sample represents those that were able to be analyzed and met our criteria at the time of publishing. This is by no means an exhaustive list, but provides a window into the security flaws most contact tracing apps contain.
Assessment Method: We conducted both static and dynamic analysis, as well as assessing whether any RASP checks were in place.
Analyzing for Key Mobile Application Hardening Techniques
Each of the categories analyzed below presents risk for mobile app security, including user location data and other information with privacy concerns attached. Without adequate protection, these apps could be tampered with or even copied and turned into “fake apps,” allowing malicious actors to trick citizens into downloading unapproved versions and giving away sensitive information.
We analyzed apps to search for six basic application hardening techniques, across two key categories:
- Name obfuscation: Name obfuscation hides identifiers in the application’s code to prevent hackers from reverse engineering and analyzing source code
- String encryption: Encrypts sensitive information included in the source code, such as API keys and cryptographic keys to prevent hackers from extracting them
- Asset / resource encryption: Encrypts assets or resources (i.e. the non-source code resources used in an app) to prevent hackers from accessing or re-using them
- Class encryption: Encrypts classes to prevent hackers from gaining insight into the internal logic of applications
Runtime Application Self-Protection (RASP)
-
Root detection: Attackers often try to “root” a device to bypass the Android application sandbox and conduct unapproved actions. Root detection monitors the environment in which applications are running and prevents them from being executed on rooted devices.
- Emulator detection: Emulators are tools that allow applications to be run on virtual devices on computers. Hackers can use these to gain insight into how they function. Emulator detection prevents applications from being executed on virtual devices.
While not an exhaustive list, these six hardening techniques are important for every mobile app. In this report, we have used them as indicators for the level of in-app security implemented within contact tracing apps. For maximum security, mobile apps need to be protected by multiple layers of security, combining the listed techniques with code hardening like arithmetic obfuscation and control flow obfuscation, plus RASP techniques such as tamper detection and hook detection.
Results: Most contact-tracing apps don’t employ sufficient hardening techniques
Similar to the financial services mobile app analysis we conducted in late 2019, it’s clear that the vast majority of contact tracing apps built and deployed by governments are not sufficiently protected against reverse engineering and potential exploitation. They are easy for hackers to decompile, attack, and even create fake clones, and are likely to lead to security breaches if they have not already.
Overall data
Here’s what the data shows:
- Only 41% have root detection
- Only 41% include some level of name obfuscation
- Only 29% include string encryption
- Only 18% include emulator detection
- Only 6% include asset / resource encryption
- Only 6% include class encryption
- Just 1 app that we analyzed was fully obfuscated and encrypted
Regional data
We also broke the data down and conducted regional analysis, to see if there were any distinct patterns across different parts of the world. This is relevant because different areas have varying regulations and norms when it comes to security and privacy.
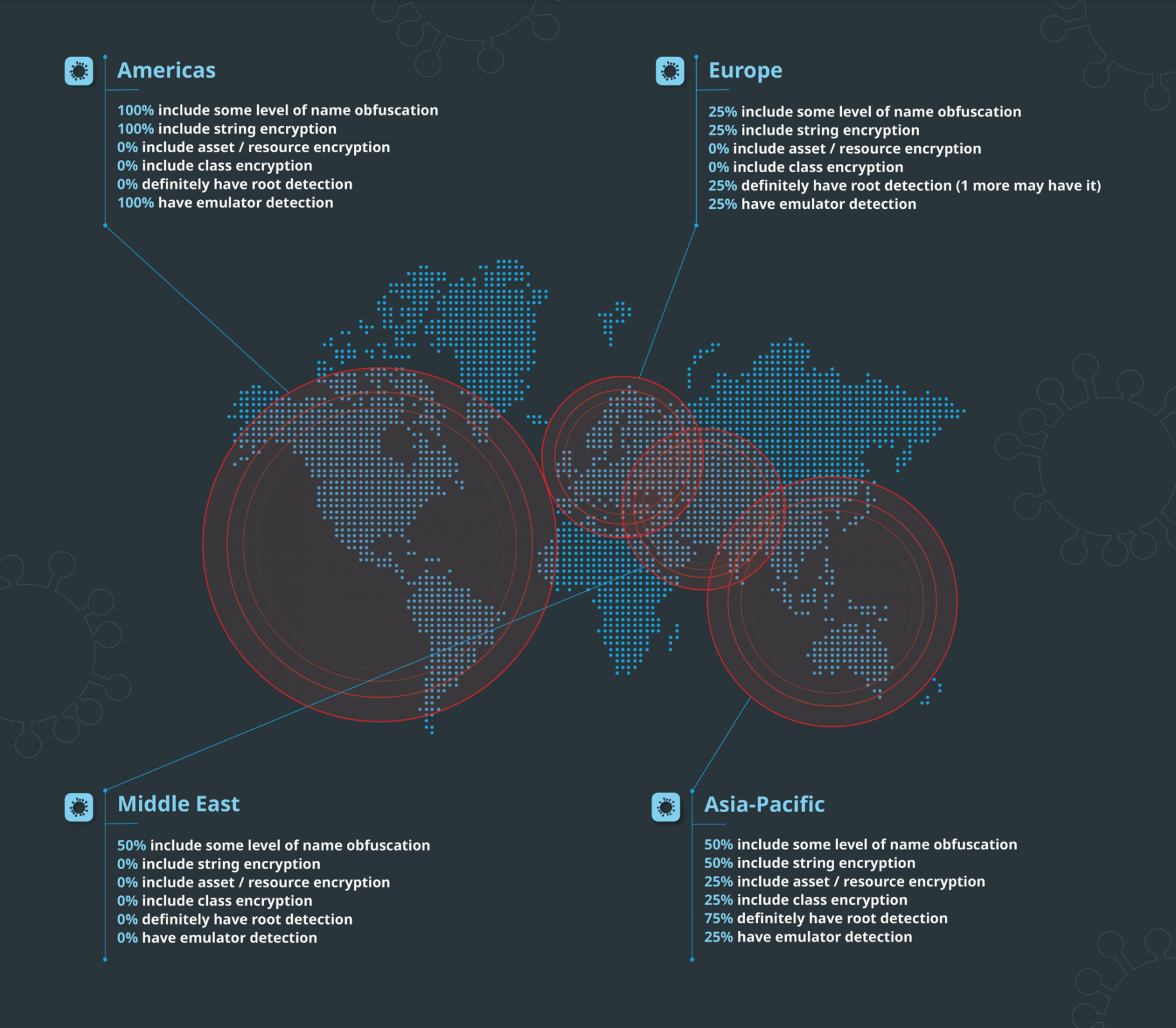
- Americas
- 100% include some level of name obfuscation
- 100% include string encryption
- 0% include asset / resource encryption
- 0% include class encryption
- 0% have root detection
- 100% have emulator detection
- Asia-Pacific
- 50% include some level of name obfuscation
- 50% include string encryption
- 25% include asset / resource encryption
- 25% include class encryption
- 75% have root detection
- 25% have emulator detection
- Europe
- 25% include some level of name obfuscation
- 25% include string encryption
- 0% include asset / resource encryption
- 0% include class encryption
- 37.5% definitely have root detection
- 25% have emulator detection
- Middle East
- 50% include some level of name obfuscation
- 0% include string encryption
- 0% include asset / resource encryption
- 0% include class encryption
- 0% have root detection
- 0% have emulator detection
Mandatory vs. voluntary tracking apps
In most cases, these apps are opt-in—but it’s worth nothing that 3 of the apps we analyzed (about 18%) are mandatory. In other words, citizens are compelled to download and use them.
The combined population of the three countries who have mandatory apps is about 1.4 billion people. Of the apps that are mandatory, just one-third (33%) use any name obfuscation or root detection, and none (0%) use any type of encryption or emulator detection.
The mandatory nature of these apps and their massive reach make the security and privacy issues we have discussed above all the more salient. It can’t be overstated the extent to which the lack of protections can erode trust in government when inevitable hacks or breaches come to light.
Why security matters for contact tracing apps
The value of trust
Contact tracing projects, in general, are only as powerful as their reach. In other words, countries and other groups attempting to roll out contact tracing programs need the vast majority of people to participate for them to be valuable.
Mobile apps are a logical vehicle for these efforts, because so many people possess smartphones today. Downloading an app is fast and easy. Again, these apps need widespread adoption, and beyond accessibility, that requires trust. It only takes a single high-profile security incident to ruin confidence in an app.
When security flaws are publicized, the whole app is suddenly distrusted and its utility wanes as users drop off. In the case of countries who build their own apps, this can erode citizen trust in the government as well, which further increases public health risks. Trust is key to success with contact tracing apps, but app makers unfortunately do not seem to be taking the risks seriously enough yet.
The real risks
Here is what governments and other organizations building COVID-19 contact tracing apps need to understand. If these apps are improperly secured (as most are), user data—in particular location information—may be at risk. This is a security issue and a major privacy concern, and can even run organizations up against compliance laws like GDPR, potentially resulting in massive fines, as well as reputational and trust issues.
Without obfuscation in place, malicious individuals may interfere with these apps for nefarious purposes, such as causing confusion, spreading false information, or instilling fear. Hacktivists, especially in places experiencing civil unrest, may also disrupt these apps—not to steal or expose data—but because they dislike the idea of government or other surveillance.
Clearly, there’s a lot at stake here. Properly securing contact tracing apps is not just a citizen privacy and security issue and a government trust issue. It’s a public health concern as well.
Best practices & how to move forward
All mobile apps—whether for mobile banking, gaming, shopping, or virus contact tracing—need to be developed securely and with a “privacy by design” ethos. Government-built and -sponsored apps, above all, should never be low-hanging fruit for hackers. Citizens who use these apps to protect themselves and the populace at large from COVID-19 should not be risking their personal privacy and safety by using them.
It’s up to governments and other entities who build these apps to ensure that the core code of the app is shielded properly, and that user information and privacy is safeguarded. Root detection and emulator detection are key ways to identify, stop, and investigate hacking against these apps as well.
In general, mobile apps require a layered approach to security. Developers should use code hardening to protect code at rest and runtime application self-protection (RASP) to protect apps in use. Beyond root detection and emulator detection, to be truly bulletproof, apps should implement hook detection, tamper detection, and debugger detection as well. They should also employ real-time mobile threat intelligence tools to understand when hackers go after apps and stop them as quickly as possible through blocking or vulnerability management strategies. Many industry standard best practices are well-known and relatively easy to implement.
We recognize that many governments employ third-party contractors to develop these apps, but this does not absolve them of responsibility. Anyone disseminating contract tracing apps must impose minimum standards of quality and security on the third parties or internal teams who are developing them.
Furthermore, when properly designed, these apps should not be gathering certain types of information, and certainly should not be storing it for any length of time. Wherever possible, the information the apps process should be treated as very sensitive, and every effort taken to ensure that the collection and potential exposure of personally identifying information is minimized.
Any organization wishing to better inform themselves about mobile app protection can reach out to the security experts at Guardsquare via our website for further information and assistance.
About Guardsquare
Guardsquare is the global leader in mobile application protection. More than 650 customers worldwide across all major industries rely on Guardsquare to secure their mobile applications against reverse engineering and hacking. Built on the open source ProGuard technology, Guardsquare software integrates transparently in the development process and adds multiple layers of protection to Android (DexGuard) and iOS (iXGuard) applications hardening them against both on-device and off-device attacks. With the addition of ThreatCast, its mobile application security console, Guardsquare offers the most complete mobile security solution on the market today. Guardsquare is based in Leuven, Belgium with a US office in Boston, MA.




