Device admin privileges
Malware often aims to become a device admin app. This status confers advanced capabilities such as wiping data; performing actions on the screen lock (i.e., changing the screen lock, setting password rules, monitoring screen unlock attempts, locking the screen, setting screen lock password expiration, etc.); setting storage encryption; disabling the camera, amongst others. All these actions are usually triggered remotely from a command-and-control admin panel. Moreover, an application cannot be uninstalled as long as it is registered as an administrator.
Obtaining device admin privileges
Obtaining device admin privileges can be achieved through:
- Nagging the user to provide privileges
- Automating through accessibility services
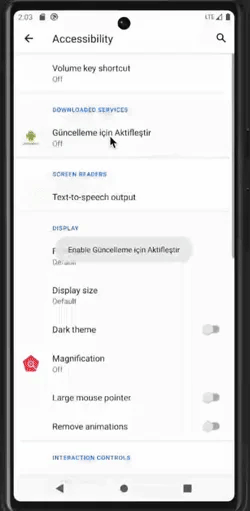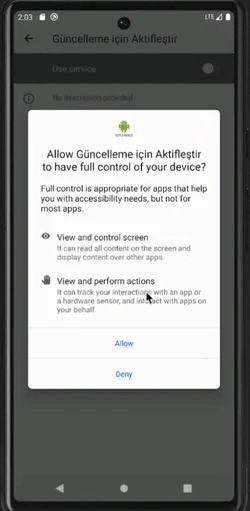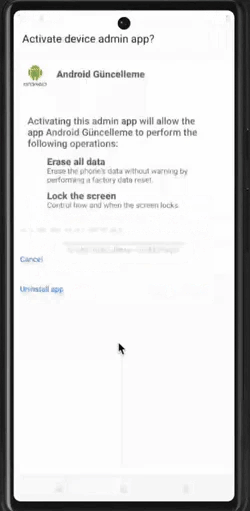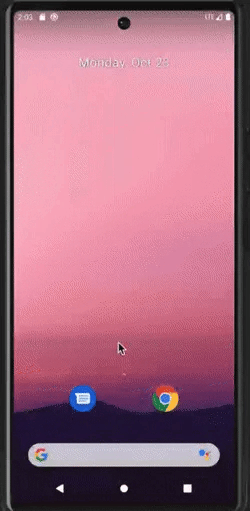
Malware is granted device admin privileges
Resisting permission revocation
Once malware obtains the device admin rights, it can resist attempts at uninstallation, privilege revocation, and more.
![]()
Attempt to uninstall a malicious application that has obtained device admin rights
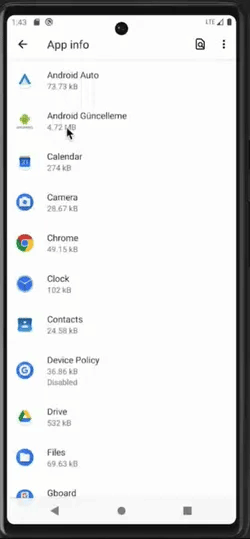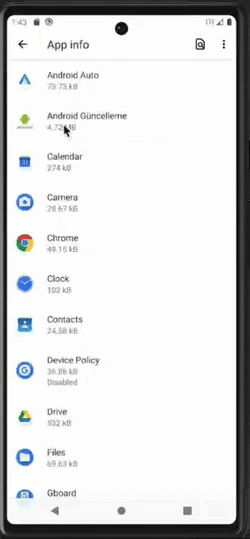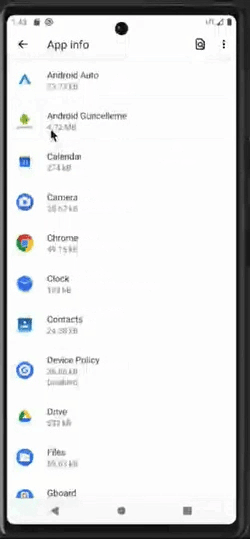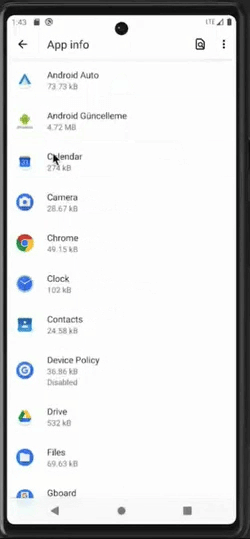
Attempt to change settings of a malicious application that has obtained device admin rights
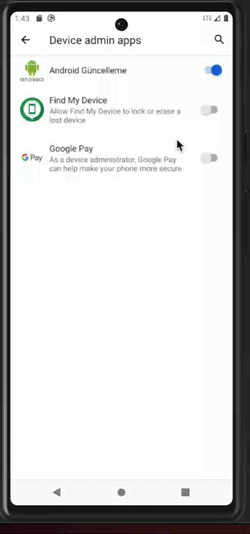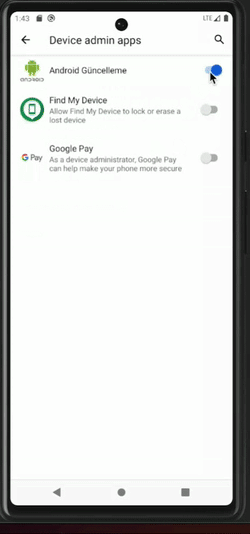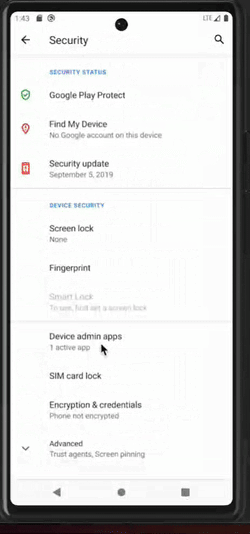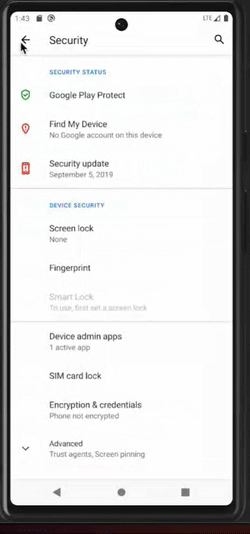
Attempt to deactivate a malicious application that has obtained device admin rights




