Security Research Center
Recent app inspection
| Technique summary | |
| Technique | Recent app inspection |
| Against | UI injections: Activity injections |
| Limitations | Requires PACKAGE_USAGE_STATS permission |
| Does not detect view injections | |
| Side effects | Low-impact false positives possible with custom launchers or repeated app switching |
| Recommendations | Recommended for use combined with other techniques |
This approach is using a thread that is active while the protected activity (for example, a login activity) is on screen. This thread is continuously examining the most recently used apps. If the package name of the most recently used app does not correspond to the app's own package name, it is considered a positive UI injection detection. The launcher and settings app can also be allowed, in order to prevent false positives, if the user switches to a different app while the login activity is on the screen.
In order to obtain the most recently used application, use the UsageStatsManager API. Thus, this requires the PACKAGE_USAGE_STATS permission.
The code to obtain the package name of the top activity is shown in the snippet below:
This code extracts the stats from the last CHECK_INTERVAL milliseconds, and sorts them according to the last time they were used.
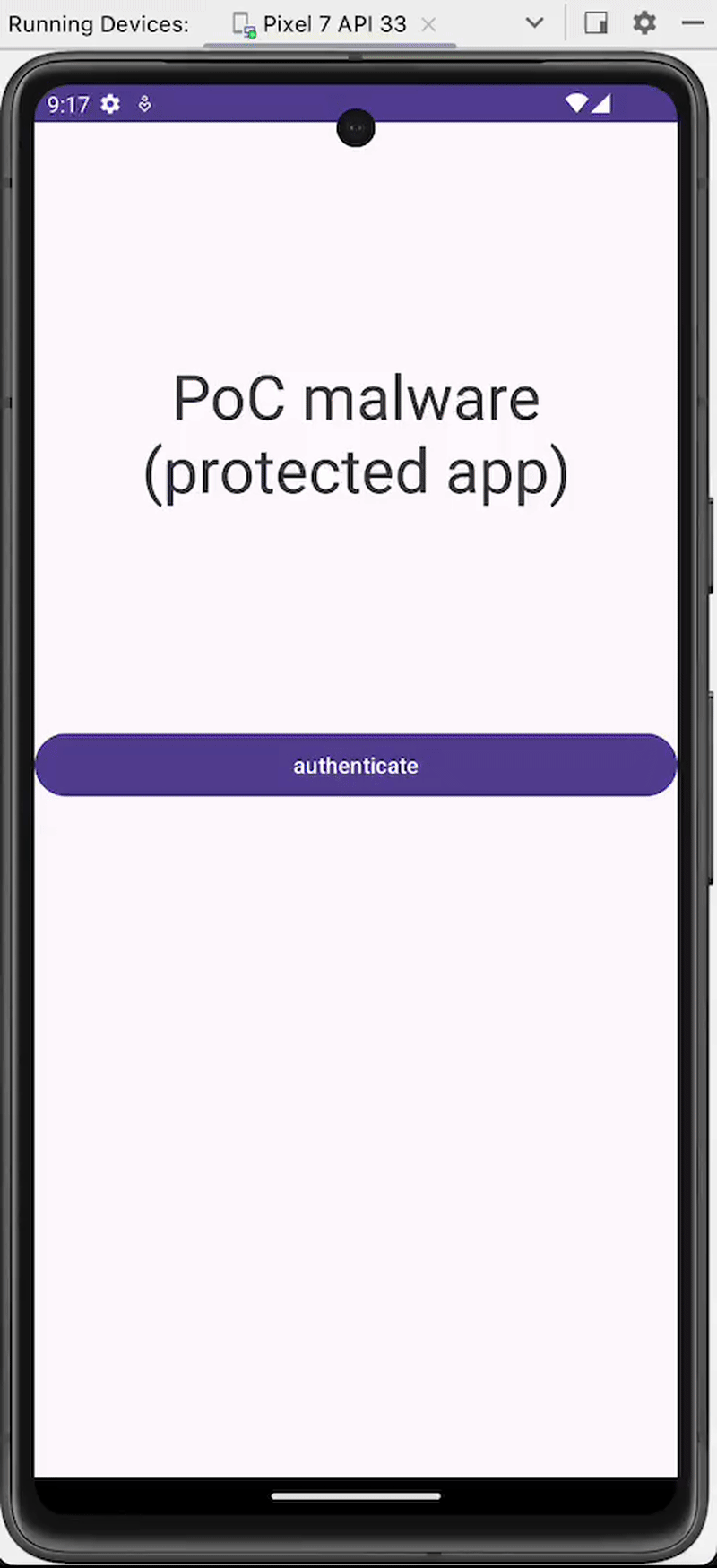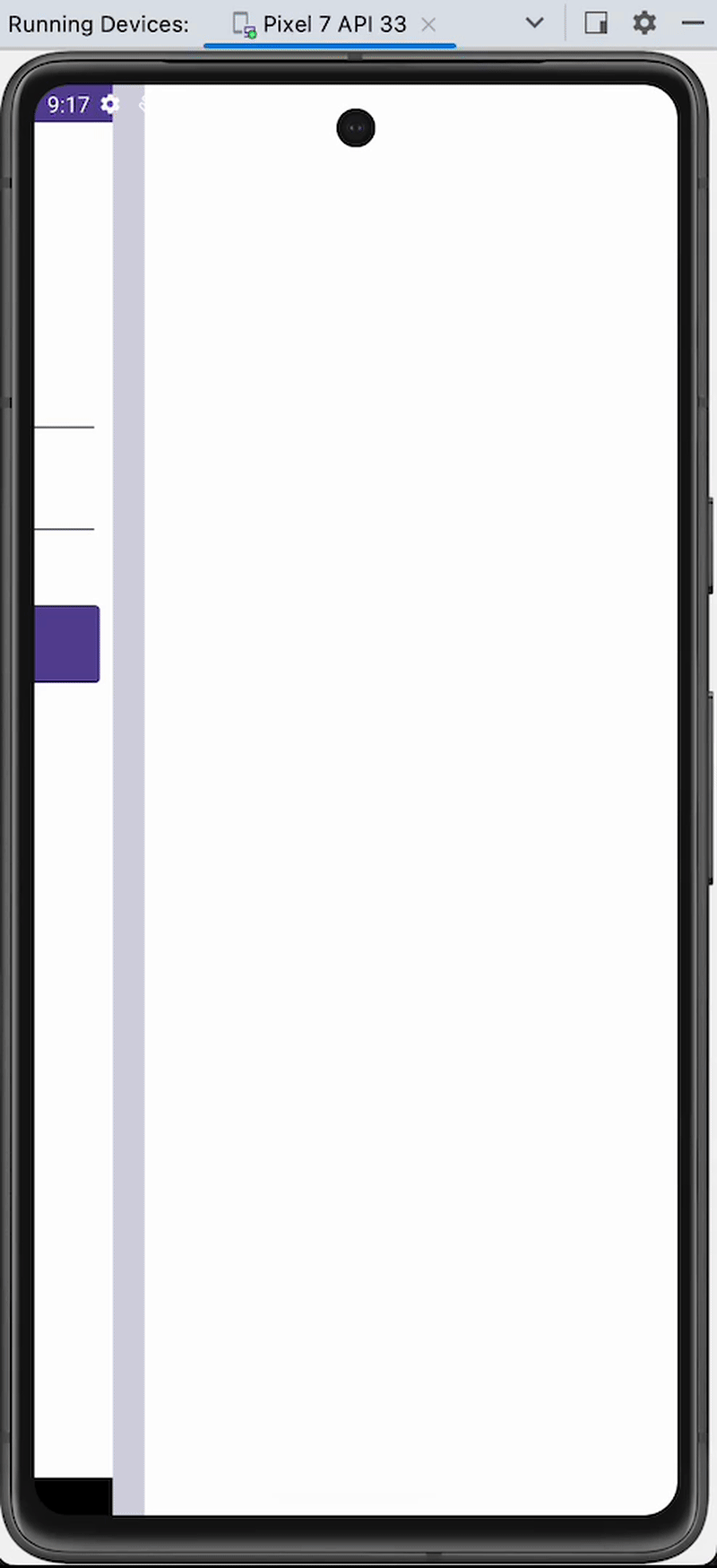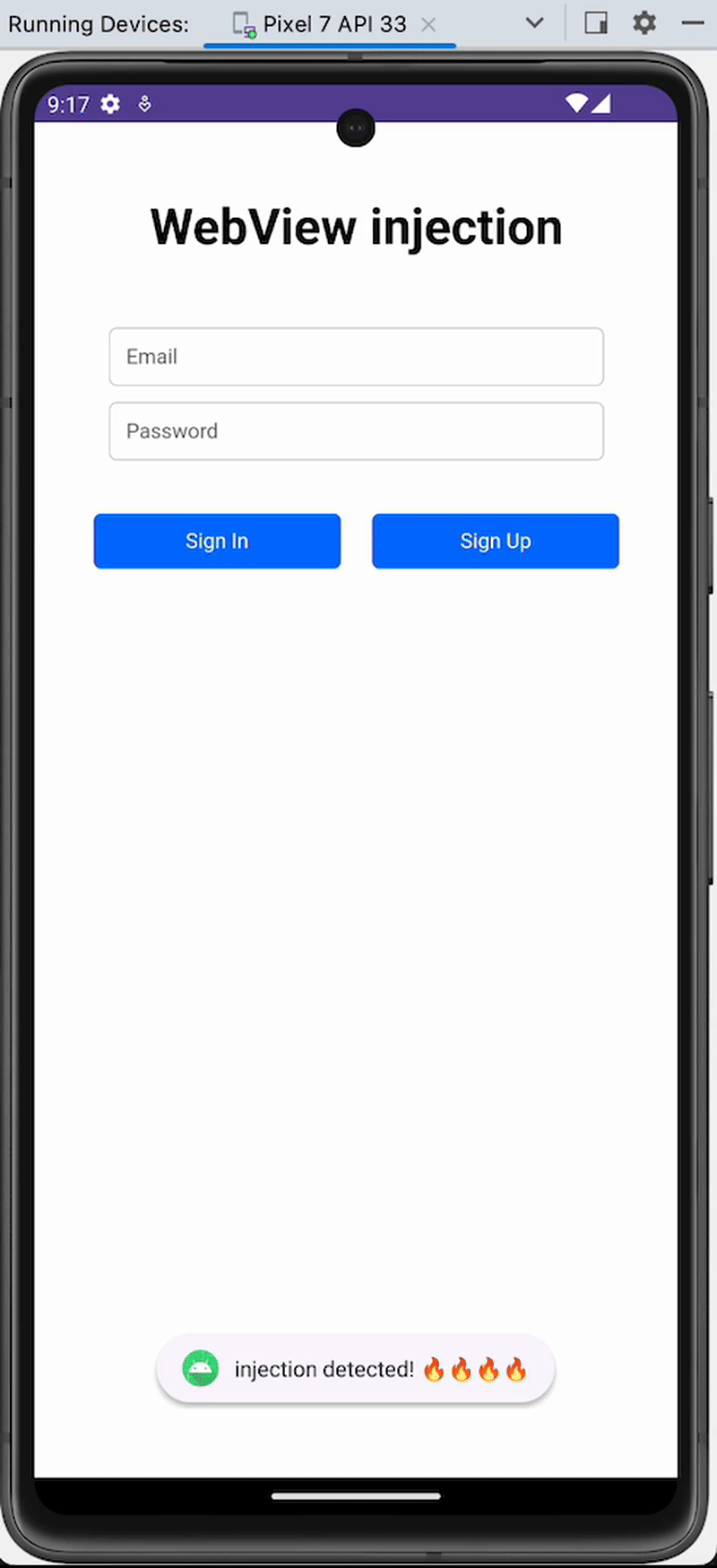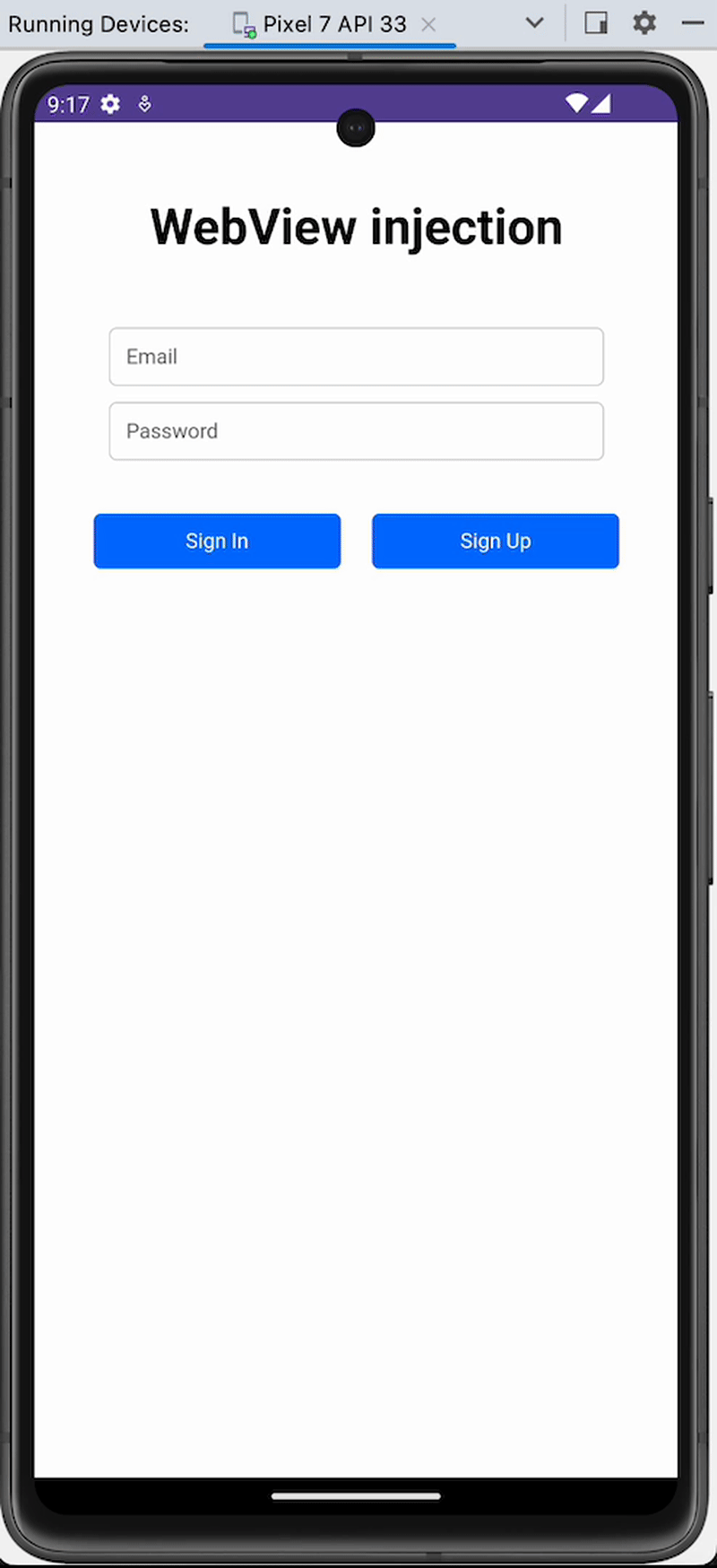
Example of implemented protection
Note
False positives may occur if the user switches to a different app while the protected activity is on screen, because the launcher will appear as the most recent app. If the launcher and the settings apps are allow-listed, false positives can still happen if the phone has configured a different launcher by default.
As the action on detection is a soft block (such as a warning message or bringing the obscured activity back on top), having a false positive does not entail severe consequences. We advise that the data related to positive checks is sent to the backend.




